
Syntax and Semantics - Benedikt Ahrens
Benedikt Ahrens Universite Nice Sophia Antipolis; Member, School of Mathematics September 25, 2012 For more videos, visit http://video.ias.edu
From playlist Mathematics

In this video I briefly go over the advantage to the Schnorr signature, and how to sign and verify.
From playlist Cryptography and Coding Theory

Logic: The Structure of Reason
As a tool for characterizing rational thought, logic cuts across many philosophical disciplines and lies at the core of mathematics and computer science. Drawing on Aristotle’s Organon, Russell’s Principia Mathematica, and other central works, this program tracks the evolution of logic, be
From playlist Logic & Philosophy of Mathematics

Introduction to Predicate Logic
This video introduces predicate logic. mathispower4u.com
From playlist Symbolic Logic and Proofs (Discrete Math)

Simplify the Negation of Statements with Quantifiers and Predicates
This video provides two examples of how to determine simplified logically equivalent statements containing quantifiers and predicates. mathispower4u.com
From playlist Symbolic Logic and Proofs (Discrete Math)

RSA SIgnature Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Fundamental concepts of Digital Signatures are discussed. ElGamal and Schnorr Digital Signature schemes are analyzed. Digital signature standard is presented.
From playlist Network Security

Fundamental concepts of Digital Signatures are discussed. ElGamal and Schnorr Digital Signature schemes are analyzed. Digital signature standard is presented.
From playlist Network Security

OWASP AppSec 2010: BitFlip: Determine a Data's Signature Coverage from Within the Application 2/2
Clip 2/2 Speaker: Henrich Christopher Poehls, University of Passau - ISL Despite applied cryptographic primitives applications are working on data that was not protected by them. We show by abstracting the message flow between the application and the underlying wire, that protection is
From playlist OWASP AppSec 2010

Benedikt Ahrens - Le principe d'univalence: le transfer du raisonnement à traver les equivalence
Le raisonnement à équivalence près est omniprésent en mathématique, et les mathématiciens le font implicitement. Pour les mathématiques sur ordinateurs, ce n'est pas si simple : il faut donner tous les détails éxplicitement. C'est pour cela que Voevodsky a créé les fondements univalents, a
From playlist Workshop Schlumberger 2022 : types dépendants et formalisation des mathématiques

Model Theory - part 01 - The Setup in Classical Set Valued Model Theory
Here we give the basic setup for Model Theory. I learned this from a talk Tom Scanlon gave in 2010 at CUNY.
From playlist Model Theory

RailsConf 2020 CE - Static Type Checking in Rails with Sorbet by Hung Harry Doan
Static Type Checking in Rails with Sorbet by Hung Harry Doan "Sorbet is a powerful static type-checking tool for Ruby. Type checking can catch errors early and improve the developer experience—and with the right tools, it can even be used with dynamic methods in Rails. In this talk, we’l
From playlist RailsConf 2020 CE
Diego Figueira: Semistructured data, Logic, and Automata – lecture 2
Semistructured data is an umbrella term encompassing data models which are not logically organized in tables (i.e., the relational data model) but rather in hierarchical structures using markers such as tags to separate semantic elements and data fields in a ‘self-describing’ way. In this
From playlist Logic and Foundations
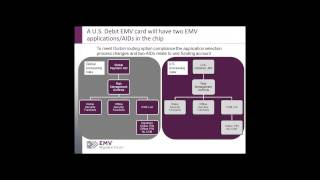
EMV 101: Fundamentals of EMV Chip Payment
Commonly used globally in place of magnetic stripe, EMV chip technology helps to reduce card fraud in a face-to-face card-present environment; provides global interoperability; and enables safer and smarter transactions across contact and contactless channels. EMV implementation was initia
From playlist Payments

Joshua Wrigley - The Logic and Geometry of Localic Morphisms
Talk at the school and conference “Toposes online” (24-30 June 2021): https://aroundtoposes.com/toposesonline/ Slides: https://aroundtoposes.com/wp-content/uploads/2021/07/WrigleySlidesToposesOnline.pdf In this presentation, a substitutive syntactic site for the classifying topos of a ge
From playlist Toposes online

Nicole Schweikardt: Databases and descriptive complexity – lecture 1
Recording during the meeting "Spring school on Theoretical Computer Science (EPIT) - Databases, Logic and Automata " the April 11, 2019 at the Centre International de Rencontres Mathématiques (Marseille, France) Filmmaker: Guillaume Hennenfent Find this video and other talks given by wor
From playlist Numerical Analysis and Scientific Computing

CERIAS Security: Traust and PeerTrust2: Applying Trust Negotiation to Real Systems 6/6
Clip 6/6 Speaker: Marianne Winslett · University of Illinois at Urbana-Champaign Automated trust negotiation is an approach to authorization for open systems, i.e., systems where resources are shared across organizational boundaries. Automated trust negotiation enables open computing
From playlist The CERIAS Security Seminars 2005 (2)

Lec 24 | MIT 6.033 Computer System Engineering, Spring 2005
Advanced Authentication View the complete course at: http://ocw.mit.edu/6-033S05 License: Creative Commons BY-NC-SA More information at http://ocw.mit.edu/terms More courses at http://ocw.mit.edu
From playlist MIT 6.033 Computer System Engineering, Spring 2005

Signing - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography
