
Subneting Explained | What Is Subneting? | How It Works? | Networking Tutorial | Simplilearn
🔥Advanced Executive Program In Cybersecurity: https://www.simplilearn.com/pgp-advanced-executive-program-in-cyber-security?utm_campaign=Subneting-mgu4blmFF_w&utm_medium=Descriptionff&utm_source=youtube 🔥Caltech Cybersecurity Bootcamp(US Only): https://www.simplilearn.com/cybersecurity-boot
From playlist Cyber Security Playlist [2023 Updated]🔥

Subsequence Definition In this video, I define the notion of a subsequence and illustrate with some examples. I also show that if a sequence converges, then any subsequence converges as well Check out my Sequences Playlist: https://www.youtube.com/watch?v=collx3am6II&list=PLJb1qAQIrmmCu
From playlist Sequences
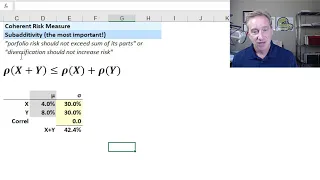
Coherent risk measures and why VaR is not coherent (FRM T4-5)
[my xls is here https://trtl.bz/2ErWQl8] Coherence requires that a risk measure meets all four of the following conditions unconditionally: 1. Translation invariance (aka, adding cash reduces risk), 2. Positive homogeneity (aka, risk is proportional to size"), 3. Monotonicity (aka, If Y do
From playlist Valuation and RIsk Models (FRM Topic 4)
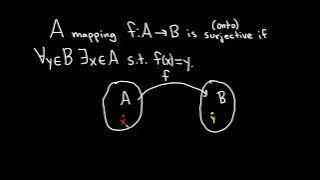
Definition of a Surjective Function and a Function that is NOT Surjective
We define what it means for a function to be surjective and explain the intuition behind the definition. We then do an example where we show a function is not surjective. Surjective functions are also called onto functions. Useful Math Supplies https://amzn.to/3Y5TGcv My Recording Gear ht
From playlist Injective, Surjective, and Bijective Functions

Ethical Hacking Tutorial | Comprehensive Subdomain Enumeration | Session 12 | #cybersecurity
Don’t forget to subscribe! This ethical hacking tutorial series is about comprehensive subdomain enumeration. Through this tutorial series, I will be demonstrating how to install, configure and use different tools for subdomain enumeration. We will try to go through the following subdom
From playlist Comprehensive Subdomain Enumeration

Welcome to Quantitative Risk Management (QRM). In this lesson we introduce the axiomatic approach to risk measures. We give the definition of risk measure and we discuss what its uses for us are in terms of reserve capital quantification. We then define coherent and convex measures. The p
From playlist Quantitative Risk Management

Matrix trace inequalities for quantum entropy - M. Berta - Main Conference - CEB T3 2017
Mario Berta (Imperial) / 11.12.2017 Title: Matrix trace inequalities for quantum entropy Abstract: I will present multivariate trace inequalities that extend the Golden-Thompson and Araki-Lieb-Thirring inequalities as well as some logarithmic trace inequalities to arbitrarily many matric
From playlist 2017 - T3 - Analysis in Quantum Information Theory - CEB Trimester

Entropy bounds for reduced density matrices of fermionic states - Elliott Lieb
Elliott Lieb Princeton Univ April 2, 2014 For more videos, visit http://video.ias.edu
From playlist Mathematics

Ethical Hacking Tutorial | Comprehensive Subdomain Enumeration | Session 16 | #cybersecurity
Don’t forget to subscribe! This ethical hacking tutorial series is about comprehensive subdomain enumeration. Through this tutorial series, I will be demonstrating how to install, configure and use different tools for subdomain enumeration. We will try to go through the following subdom
From playlist Comprehensive Subdomain Enumeration

Bit threads and holographic monogamy by Matthew Headrick
ORGANIZERS : Pallab Basu, Avinash Dhar, Rajesh Gopakumar, R. Loganayagam, Gautam Mandal, Shiraz Minwalla, Suvrat Raju, Sandip Trivedi and Spenta Wadia DATE : 21 May 2018 to 02 June 2018 VENUE : Ramanujan Lecture Hall, ICTS Bangalore In the past twenty years, the discovery of the AdS/
From playlist AdS/CFT at 20 and Beyond

Quenched large deviations for random motions in degenerate random media by Chiranjib Mukherjeer
Large deviation theory in statistical physics: Recent advances and future challenges DATE: 14 August 2017 to 13 October 2017 VENUE: Madhava Lecture Hall, ICTS, Bengaluru Large deviation theory made its way into statistical physics as a mathematical framework for studying equilibrium syst
From playlist Large deviation theory in statistical physics: Recent advances and future challenges
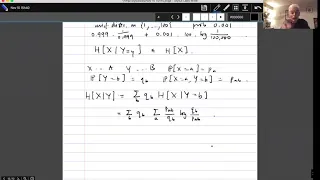
Topics in Combinatorics lecture 11.1 --- Subadditivity of entropy and Shearer's lemma
A useful rule that is satisfied by entropy is that if X_1,...,X_n are random variables, then H[X_1,...,X_n] is at most H[X_1]+...+H[X_n]. Shearer's lemma is a generalization of this, where one compares H[X_1,...,X_n] by a suitable weighted average of joint entropies of the form H[X_i : i i
From playlist Topics in Combinatorics (Cambridge Part III course)

Ethical Hacking Tutorial | Comprehensive Subdomain Enumeration | Session 08 | #cybersecurity
Don’t forget to subscribe! This ethical hacking tutorial series is about comprehensive subdomain enumeration. Through this tutorial series, I will be demonstrating how to install, configure and use different tools for subdomain enumeration. We will try to go through the following subdom
From playlist Comprehensive Subdomain Enumeration

Ethical Hacking Tutorial | Comprehensive Subdomain Enumeration | Session 10 | #cybersecurity
Don’t forget to subscribe! This ethical hacking tutorial series is about comprehensive subdomain enumeration. Through this tutorial series, I will be demonstrating how to install, configure and use different tools for subdomain enumeration. We will try to go through the following subdom
From playlist Comprehensive Subdomain Enumeration

Ethical Hacking Tutorial | Comprehensive Subdomain Enumeration | Session 17 | #cybersecurity
Don’t forget to subscribe! This ethical hacking tutorial series is about comprehensive subdomain enumeration. Through this tutorial series, I will be demonstrating how to install, configure and use different tools for subdomain enumeration. We will try to go through the following subdom
From playlist Comprehensive Subdomain Enumeration

Measure Theory 2.3 : Open and Closed Inervals are Lebesgue Measurable
In this video, I prove that the open and closed intervals (a, b) and [a, b] (as well as [a, b) and (a, b]) are in fact Lebesgue measurable, and thus validating the previous video in this series. Email : fematikaqna@gmail.com Code : https://github.com/Fematika/Animations Notes : None yet
From playlist Measure Theory

Ethical Hacking Tutorial | Comprehensive Subdomain Enumeration | Session 13 | #cybersecurity
Don’t forget to subscribe! This ethical hacking tutorial series is about comprehensive subdomain enumeration. Through this tutorial series, I will be demonstrating how to install, configure and use different tools for subdomain enumeration. We will try to go through the following subdom
From playlist Comprehensive Subdomain Enumeration

(PP 1.5) Measure theory: Basic Properties of Measures
(0:00) Lebesgue measure. (4:33) Basic Properties of Measures: Monotonicity, Subadditivity. A playlist of the Probability Primer series is available here: http://www.youtube.com/view_play_list?p=17567A1A3F5DB5E4 You can skip the measure theory (Section 1) if you're not intereste
From playlist Probability Theory

Andreas Winter: "Entropy inequalities beyond strong subadditivity"
Entropy Inequalities, Quantum Information and Quantum Physics 2021 "Entropy inequalities beyond strong subadditivity" Andreas Winter - Universitat Autònoma de Barcelona Abstract: What are the constraints that the von Neumann entropies of the 2^n possible marginals of an n-party quantum s
From playlist Entropy Inequalities, Quantum Information and Quantum Physics 2021

Ethical Hacking Tutorial | Comprehensive Subdomain Enumeration | Session 18 | #cybersecurity
Don’t forget to subscribe! This ethical hacking tutorial series is about comprehensive subdomain enumeration. Through this tutorial series, I will be demonstrating how to install, configure and use different tools for subdomain enumeration. We will try to go through the following subdom
From playlist Comprehensive Subdomain Enumeration