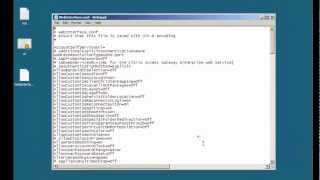
Citrix : Web Interface website for the Citrix Access Gateway
More videos like this online at http://www.theurbanpenguin.com Here we take a look at creating a Citrix Web Interface web site to support the Citrix Access Gateway. In doing so we will also look at the importance of backing up the webinterface.conf and using that as a template fro new site
From playlist Citrix

Citrix : Web Interface enabling HTTPS
More videos like this online at http://www.theurbanpenguin.com In this video we take a look at enabling HTTPS access with SSL to the WebInterface Server. With the later Citrix Receivers HTTPS is becoming the Protocol of choice and certainly when used with the Citrix Access Gateway we shoul
From playlist Citrix

An intro to the core protocols of the Internet, including IPv4, TCP, UDP, and HTTP. Part of a larger series teaching programming. See codeschool.org
From playlist The Internet

AT&T: The Company Behind the Telephone
📚 If you enjoyed this video about AT&T and want to learn even more, we recommend you read the book "End of the Line: The Rise and Fall of AT&T" by Cauley Leslie 👉 https://amzn.to/3c7QR1p (Note: As an Amazon Associate, we earn from qualifying purchases). Your support makes our content poss
From playlist Vintage Telephone; AT&T; Bell Labs; Telecommunications; Satellites:

Ever heard of Quantum Operators and Commutators? (Explained for Beginners)!
What is a quantum operator? And just how useful are quantum commutators? Find out how they help us understand the Ehrenfest Theorem! Hi everyone, I'm back with a new video! This time it's the first in a two-part mini-series on one of the coolest theorems in quantum mechanics - Ehrenfest's
From playlist Quantum Physics by Parth G

AT&T Archives: What is the Bell System?
For more from the AT&T Archives, see http://techchannel.att.com/showpage.cfm?ATT-Archives The Bell System, which in 1976 employed nearly one million people at 27,000 locations worldwide, always benefited from explaining its scope to the public. This explanation is from a blue-collar POV,
From playlist Vintage Telephone; AT&T; Bell Labs; Telecommunications; Satellites:

Certificate Services: Stand-alone Certificate Authority
Certificate Services: Stand-alone Certificate Authority, CA
From playlist Cryptography, Security

Black Hat USA 2010: Becoming the Six Million Dollar Man 4/6
Speaker: Gunter Ollmann Starting a life of Internet crime is easy; in fact you've probably already doing it as far as the RIAA is concerned. Now that you've chosen to embark upon a new career, how are you going to get dirty, filthy, stinking rich? How do you become a millionaire? The tool
From playlist BH USA 2010 - BIG PICTURE

Omar Mohsen: Characterization of Maximally Hypoelliptic Differential Operators
Talk by Omar Mohsen in Global Noncommutative Geometry Seminar (Americas) on September 16, 2022, https://globalncgseminar.org/talks/talk-by-omar-mohsen/
From playlist Global Noncommutative Geometry Seminar (Americas)

Botleggers Exposed - Analysis of The Conti Leaks Malware
Join us for analysis of the leaked Conti malware, what is BazarLoader, how is Conti operated, and what does all this mean for your security team. These are our first thoughts as the situation unfolds... Twitter account for the leaker: https://twitter.com/ContiLeaks ----- OALABS DISCORD h
From playlist Open Analysis Live!

The Craziest Ponzi Schemes in History. Top Ten True Crime Stories. A hundred years ago in 1920, Charles Ponzi became famous when his investment scheme collapsed. Ponzi promised to double investors money in three months, at his peak he brought in more than $2 million per week at his offic
From playlist Top Ten Lists

Brucon 2010: Memoirs of a Data Security Street Fighter 4/5
Speaker: Mikko Hypponen 20 years, and what have we got? - Where did we go wrong? - Why can't we fix these things? - Is it going to get better or worse? More information be found via the Brucon website: http://bit.ly/brucon2010 Source: http://bit.ly/brucon2010_videos
From playlist Brucon 2010

Webinar: Authorizing Access to Science Gateway Resources
Presented by Jim Basney of NCSA & Trusted CI, Marlon Pierce of Indiana University & SGCI, and Tom Barton of the University of Chicago & Internet2 Presentation slides are available on our website: https://sciencegateways.org/-/authorizing-access-to-science-gateway-resources Data use agree
From playlist Center for Applied Cybersecurity Research (CACR)

An Introduction to Functional Programming
We've all heard of functional programming, but how can you apply it to your existing code? In this talk by Eric Normand, author of 📖 Grokking Simplicity | http://mng.bz/oGXN 📖 DISCOUNT CODE ⭐ WATCHNORMAND40 ⭐ you will learn to identify the hardest code to test, make it more testabl
From playlist Functional Programming
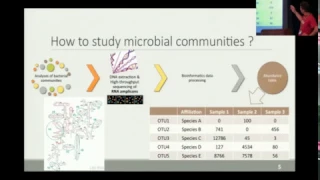
FROGS Find Rapidly OTU with Galaxy Solution, 20160628
Galaxy Community Conference 2016, Indiana University - Bloomington | https://gcc2016.iu.edu/ https://gcc16.sched.com/event/3708f8eb14531cffedf3c29aed075a43# Authors: Frederic ESCUDIE, INRA Toulouse Lucas AUER, INRA Toulouse Maria BERNARD, INRA Jouy-en-Josas Laurent CAUQUIL, INRA Toulouse
From playlist 2016 Galaxy User Community Conference (GCC16)
From playlist Open Q&A

DEFCON 13: Mosquito - Secure Remote Code Execution Framework
Speakers: Wes Brown, Senior Security Consultant Scott Dunlop, Security Researcher Mosquito is a lightweight framework to deploy and run code remotely and securely in the context of penetration tests. It makes a best effort to ensure that the communications are secure. Special care is tak
From playlist DEFCON 13


