
An informal introduction to cryptography. Part of a larger series teaching programming at http://codeschool.org
From playlist Cryptography

Steganography Tutorial - Hide Messages In Images
Steganography is the hiding of a secret message within an ordinary message and the extraction of it at its destination. Steganography takes cryptography a step further by hiding an encrypted message so that no one suspects it exists. Ideally, anyone scanning your data will fail to know it
From playlist Ethical Hacking & Penetration Testing - Complete Course
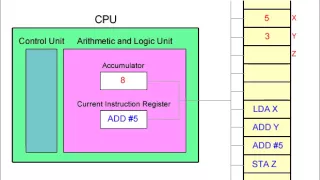
Fetch Decode Execute Cycle and the Accumulator
This (silent) video illustrates the fetch decode execute cycle. A simplified view of the CPU focusses on the role of the accumulator register when a program runs. For simplicity, the machine code commands being executed are represented by assembly language code. This assembly language co
From playlist Computer Hardware and Architecture

Cryptanalysis of Classical Ciphers
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

!!Con West 2020 - isis agora lovecruft: big number small computer
Presented at !!Con West 2020: http://bangbangcon.com/west isis agora lovecruft's keynote, big number small computer! #bangbangcon #bangbangconwest #bangbangconwest2020
From playlist !!Con West 2020

Primality (1 of 2: Fermat's Test)
From playlist Cryptography

Entropy accumulation - O. Fawzi - Workshop 2 - CEB T3 2017
Omar Fawzi / 23.10.17 Entropy accumulation We ask the question whether entropy accumulates, in the sense that the operationally relevant total uncertainty about an n-partite system A=(A1,…An) corresponds to the sum of the entropies of its parts Ai. The Asymptotic Equipartition Property i
From playlist 2017 - T3 - Analysis in Quantum Information Theory - CEB Trimester

Stanford Webinar - Latest Developments in Cryptography with Dan Boneh
Learn more at https://online.stanford.edu/programs/stanford-advanced-cybersecurity-certificate?utm_source=youtube&utm_medium=social&utm_campaign=webinar In this webinar, you’ll learn the latest on all things “crypto” from Professor Dan Boneh, head of the Stanford’s applied cryptography gr
From playlist Stanford Webinars

Sonia Belaïd - Schémas symétriques prouvés sûrs contre les attaques par canaux auxiliaires
Schémas symétriques prouvés sûrs contre les attaques par canaux auxiliaires
From playlist Journées Codage et Cryptographie 2014

Blackhat Europe 2010: Changing Threats To Privacy: From TIA to Google 3/7
Clip 3/7 Speaker: Moxie Marlinspike We won the war for strong cryptography, anonymous darknets exist in the wild today, and decentralized communication networks have emerged to become reality. These strategies for communicating online were conceived of in anticipation of a dystopian futur
From playlist Black Hat Europe 2010

Ethical Hacking Tutorial Basics-Why, what, how? | Ethical Hacking Training | Edureka Ethical Hacking
🔥Edureka Online Training: https://www.edureka.co/cybersecurity-certification-training This Edureka "Ethical Hacking Tutorial" LIVE session will give you an introduction to Ethical Hacking. This video will give you an exhaustive video on key topics of Ethical Hacking for beginners! 🔵 PGP
From playlist Edureka Live Classes 2020

Few other Cryptanalytic Techniques
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Symmetric Cryptosystems - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Ethical Hacking Tutorial For Beginners | Ethical Hacking Course | Ethical Hacking Training | Edureka
🔥Edureka Cyber Security Course: https://www.edureka.co/cybersecurity-certification-training 🔵 Edureka Cyber Security Masters Program: https://bit.ly/3pfHHIN This Edureka "Ethical Hacking Tutorial" video will give you an introduction to Ethical Hacking. This video will give you an exhaustiv
From playlist Cyber Security Training for Beginners | Edureka

Source Boston 2010: Changing Threats To Privacy: From TIA to Google 3/6
Clip 3/6 Speaker: Moxie Marlinspike A lot has changed since discussions around digital privacy began. The security community won the war for strong cryptography, anonymous darknets which presumably make the eradication of information impossible have been successfully deployed, and much of
From playlist SOURCE Boston 2010

Implementation of Elliptic Curve Cryptography
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

This video gives a general introduction to cryptography WITHOUT actually doing any math. Terms covered include cryptology vs cryptography vs cryptanalysis, symmetric vs public key systems, and "coding theory." NOTE: Yes, I said and wrote "cryptOanalysis" when it's actually "cryptanalysis
From playlist Cryptography and Coding Theory

Discrete Math You Need to Know - Tim Berglund
From OSCON 2013: What do you need to know about prime numbers, Markov chains, graph theory, and the underpinnings of public key cryptography? Well, maybe more than you think! In this talk, we'll explore the branch of mathematics that deals with separate, countable things. Most of the math
From playlist Open Source Convention (OSCON) 2013

