Cryptographic Hash Functions: Part 2
Cryptographic Hash Functions Applications of Crypto Hash Functions Birthday Problem Secure Hash Algorithm (SHA)
From playlist Network Security

Cryptographic Hash Functions: Part 1
Cryptographic Hash Functions Applications of Crypto Hash Functions Birthday Problem Secure Hash Algorithm (SHA)
From playlist Network Security

An informal introduction to cryptography. Part of a larger series teaching programming at http://codeschool.org
From playlist Cryptography

Primality (1 of 2: Fermat's Test)
From playlist Cryptography

What Is Hashing? | What Is Hashing With Example | Hashing Explained Simply | Simplilearn
🔥Advanced Executive Program In Cybersecurity: https://www.simplilearn.com/pgp-advanced-executive-program-in-cyber-security?utm_campaign=WhatIsHashing&utm_medium=Descriptionff&utm_source=youtube 🔥Caltech Cybersecurity Bootcamp(US Only): https://www.simplilearn.com/cybersecurity-bootcamp?utm
From playlist Cyber Security Playlist [2023 Updated]🔥
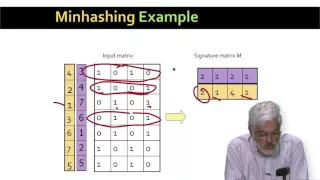
MIT 6.006 Introduction to Algorithms, Spring 2020 Instructor: Jason Ku View the complete course: https://ocw.mit.edu/6-006S20 YouTube Playlist: https://www.youtube.com/playlist?list=PLUl4u3cNGP63EdVPNLG3ToM6LaEUuStEY Hashing allows for faster search and dynamic operations on data structur
From playlist MIT 6.006 Introduction to Algorithms, Spring 2020

Lec 8 | MIT 6.046J / 18.410J Introduction to Algorithms (SMA 5503), Fall 2005
Lecture 08: Universal Hashing, Perfect Hashing View the complete course at: http://ocw.mit.edu/6-046JF05 License: Creative Commons BY-NC-SA More information at http://ocw.mit.edu/terms More courses at http://ocw.mit.edu
From playlist MIT 6.046J / 18.410J Introduction to Algorithms (SMA 5503),

MIT 6.046J Design and Analysis of Algorithms, Spring 2015 View the complete course: http://ocw.mit.edu/6-046JS15 Instructor: Ling Ren In this recitation, problems related to dynamic programming are discussed. License: Creative Commons BY-NC-SA More information at http://ocw.mit.edu/terms
From playlist MIT 6.046J Design and Analysis of Algorithms, Spring 2015

Hash tables in 4 minutes. Code: https://github.com/msambol/youtube/blob/master/data_structures/hash_table.py Sources: 1. https://www.amazon.com/Introduction-Algorithms-3rd-MIT-Press/dp/0262033844 2. https://wiki.python.org/moin/TimeComplexity 3. https://stackoverflow.com/questions/20612
From playlist Data Structures // Michael Sambol

Nexus Trimester - Graham Cormode (University of Warwick) 1/2
Stream, sketching and Big Data - 1/2 Graham Cormode (University of Warwick) 1/2 March 08, 2016 Abstract: A fundamental challenge in processing the massive quantities of information generated by modern applications is in extracting suitable representations of the data that can be stored, m
From playlist 2016-T1 - Nexus of Information and Computation Theory - CEB Trimester

Hash Tables and Hash Functions
This computer science video describes the fundamental principles of the hash table data structure which allows for very fast insertion and retrieval of data. It covers commonly used hash algorithms for numeric and alphanumeric keys and summarises the objectives of a good hash function. Co
From playlist Data Structures