
Cryptographic Hash Functions: Part 1
Cryptographic Hash Functions Applications of Crypto Hash Functions Birthday Problem Secure Hash Algorithm (SHA)
From playlist Network Security

Cryptographic Hash Functions: Part 2
Cryptographic Hash Functions Applications of Crypto Hash Functions Birthday Problem Secure Hash Algorithm (SHA)
From playlist Network Security

An informal introduction to cryptography. Part of a larger series teaching programming at http://codeschool.org
From playlist Cryptography
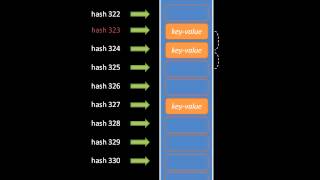
Introductory coverage of fundamental data structures. Part of a larger series teaching programming. Visit http://codeschool.org
From playlist Data Structures

Hash Tables and Hash Functions
This computer science video describes the fundamental principles of the hash table data structure which allows for very fast insertion and retrieval of data. It covers commonly used hash algorithms for numeric and alphanumeric keys and summarises the objectives of a good hash function. Co
From playlist Data Structures

Top Hashing Techniques | Popular Hashing Techniques | Network Security | #Shorts | Simplilearn
🔥FREE Cyber Security Course: https://www.simplilearn.com/learn-cyber-security-basics-skillup?utm_campaign=TopHashingTechniquesShorts&utm_medium=ShortsDescription&utm_source=youtube In this video on the top hashing techniques, we are going to take a look at the five most secure hashing alg
From playlist #Shorts | #Simplilearn

Cascadia Ruby 2014- Cloning the Seattle Ruby Brigade
By, Miles Forrest Do you love Ruby? Do you like geeking out with other Ruby coders? Do you have a project you would love to build but might need some help making it happen? The Seattle Ruby Brigade is arguably the most successful Ruby User Group in the world. They were not only the first
From playlist Cascadia Ruby 2014

Excel Hash 2021- Cooking up a quick analysis with raw data in Excel - Irish Leaving Cert data
#Excelhash Have you ever used the EVEN function, or cut out people in Excel? Well dohhhhh neither have I. But when Oz du Soleil sent me a list of ingredients for the Excel hash challenge I had to give it a go. In this video, as my submission to Excel Hash 2021, I have used cut out people
From playlist Excel Hash 2021

This is a short video tutorial on multiplying decimals. For interactive applets, worksheets, and more videos go to http://www.mathvillage.info
From playlist All about decimals

LA Ruby Conference 2013 People who liked this talk also liked ... Building Recommendation...
Title: People who liked this talk also liked ... Building Recommendation Systems Using Ruby Presented by: Ryan Weald From Amazon, to Spotify, to thermostats, recommendation systems are everywhere. The ability to provide recommendations for your users is becoming a crucial feature for mode
From playlist Los Angeles Ruby Conf 2013

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Network Analysis. Lecture 7. Structural Equivalence and Assortative Mixing
Structural and regular equivalence. Similarity metrics. Correlation coefficient and cosine similarity. Assortative mixing and homophily. Modularity. Assortativity coefficient. Mixing by node degree. Assortative and disassortative networks Lecture slides: http://www.leonidzhukov.net/hse/20
From playlist Structural Analysis and Visualization of Networks.

Wei Wang: "Alignment-free RNASeq Analysis"
Computational Genomics Summer Institute 2016 "Alignment-free RNASeq Analysis" Wei Wang, UCLA Institute for Pure and Applied Mathematics, UCLA July 22, 2016 For more information: http://computationalgenomics.bioinformatics.ucla.edu/
From playlist Computational Genomics Summer Institute 2016

How do I... FIND SPEARMAN'S RHO in Jamovi? (2022)
What if my correlation variables violate normality assumptions or I have ordinal level variables? What sort of analysis/statistic can I use? I have the answers and more in this next episode of learning stats with Jamovi! Jamovi stats: https://www.jamovi.org/ NOTE: My tutorials always us
From playlist Jamovi 2022 Tutorials

The Most Frivolous Lawsuits Ever
⭐️ Get my videos early & ad free (plus my exclusives!) only on Nebula. Save $10 per year! https://legaleagle.link/getnebula ⭐️ Some lawsuits have merit. These ones...don't. 📚 Get a free trial of Skillshare Premium: https://legaleagle.link/skillshare 🚀 Watch my next video early & ad-f
From playlist Legal Entertainment!

The 1983 "Gimli Glider" Incident.
Captain Sully’s US Airways Flight 1549 lost its engines almost immediately after takeoff, after reaching an altitude of only 2,800 feet. In 1983, a very different flight lost power at a staggering 41,000 feet, and the pilots had no choice but to try to land the plane without engines. Che
From playlist Disasters and History
Many-Facet Rasch Measurement Using Facets Software
In this video, I demonstrate how to carry out a Many-Facet Rasch Measurement Using Facets Software. If you have not watched the previous videos on Rasch measurement, they can be found from the links below: 1. https://www.youtube.com/watch?v=FDUYm7ZhXkw&t=49s 2. https://www.youtube.com/watc
From playlist Rasch Measurement


