What Is Checksum Error Detection? | What Is Checksum And How It Works? | Simplilearn
"In this video on 'What Is Checksum?', we will look at one of the most applied error-detection methods of the network domain, the checksum method, along with details and the working steps of the checksum method. Topics covered in this video on 'What Is Checksum?' are as follows: 00:00:00
From playlist Networking

Checksum is a method of checking for errors in a communications system. I'm Mr. Woo and my channel is all about learning - I love doing it, and I love helping others to do it too. I guess that's why I became a teacher! I hope you get something out of these videos - I upload almost every w
From playlist Communications & Network Systems

An intro to the core protocols of the Internet, including IPv4, TCP, UDP, and HTTP. Part of a larger series teaching programming. See codeschool.org
From playlist The Internet

Staysafe.org: Protect your computer
The Internet is a global network that connects us to limitless information and opportunities. But there are risks involved with connecting to the Internet, such as downloading viruses and spyware onto computers and devices. Watch this video for four easy steps to help protect your computer
From playlist awareness

An intro to the core protocols of the Internet, including IPv4, TCP, UDP, and HTTP. Part of a larger series teaching programming. See codeschool.org
From playlist The Internet
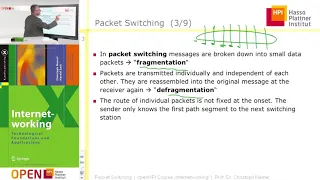
An intro to the core protocols of the Internet, including IPv4, TCP, UDP, and HTTP. Part of a larger series teaching programming. See codeschool.org
From playlist The Internet

CS105: Introduction to Computers | 2021 | Lecture 20.2 Computer Security: Mechanisms
Patrick Young Computer Science, PhD This course is a survey of Internet technology and the basics of computer hardware. You will learn what computers are and how they work and gain practical experience in the development of websites and an introduction to programming. To follow along wi
From playlist Stanford CS105 - Introduction to Computers Full Course

Checksums and Hamming distance
The term "checksum" can refer to all sorts of different error detection codes. How are some better than others? What types of errors are they good at detecting? And how do you calculate different types of checksums? Support these videos on Patreon: https://www.patreon.com/beneater or http
From playlist Error detection

26C3: Exposing Crypto Bugs through reverse engineering 4/5
Clip 4/5 Speaker: Philippe Oechslin Breaking good crypto is hard. It takes a genius to find a flaw in AES or Blowfish. On the other hand, it is also difficult to program cryptography correctly. Thus the simpler way of breaking a cryptographic software is often to reverse engineer it a
From playlist 26C3: Here be dragons day 1

DEFCON 20: No More Hooks: Detection of Code Integrity Attacks
Speakers: XENO KOVAH THE MITRE CORPORATION COREY KALLENBERG THE MITRE CORPORATION Hooking is the act of redirecting program control flow somewhere other than it would go by default. For instance code can be "inlined hooked" by rewriting instructions to unconditionally transfer to other co
From playlist DEFCON 20

The Internet: Crash Course Computer Science #29
Today, we're going to talk about how the Internet works. Specifically, how that stream of characters you punch into your browser's address bar, like "youtube.com", return this very website. Just to clarify we're talking in a broader sense about that massive network of networks connecting m
From playlist Computer Science

Bitcoin Q&A: Why is Seed Splitting a Bad Idea?
Why is dividing seed words and storing them in different locations a bad idea? Why is this a loss in security? How is this less secure as compared to Shamir's Secret Sharing? Chapters 0:00 A friend had the idea to achieve two out of three protection from my wallet seed by storing the seed
From playlist English Subtitles - aantonop Videos with subtitles in English

Introduction to TCP/IP and Sockets, part 1: Introducing the protocols and API
This is a basic introduction to the Internet protocols and how to use them in programs using sockets. This is the first of two introduction videos on the Internet Protocol and its family of associated protocols (UDP, TCP, etc.) as well as Sockets, a pseudo-standard interface made for prog
From playlist Introduction to TCP/IP and Sockets

Office Hours SWIP - Mats Rynge
ResearchSOC - Office Hours SWIP - Mats Rynge
From playlist Center for Applied Cybersecurity Research (CACR)

Computer Literacy - (unit 4) - the internet - 3 of 4
Forth unit of a series for newbie computer users. See http://proglit.com/computer-skills/ for additional information and material.
From playlist Computer Literacy - (unit 4) - the internet

Can You Validate These Emails?
Email Validation is a procedure that verifies if an email address is deliverable and valid. Can you validate these emails?
From playlist Fun

Discrete Structures: Random number generators, checksums, hashing
Learn about random number generators, checksums, and hashing. We'll start with the von Neumann random number generator and the contemporary linear congruential generator. Then we'll go over the Luhn algorithm used for credit card number validation and then introduce hash functions such as
From playlist Discrete Structures, Spring 2022