
In this video I briefly explain what minimum distance is and why it is helpful. Then I explain how to find it "the long way" and the "shortcut." Also during the process, I explain what Hamming Weight and Distance are and how to find them. Codewords from Generating Matrix Video: https://w
From playlist Cryptography and Coding Theory

2 2 Computing Minimum Edit Distance 5 54
From playlist CS124 - Full Course
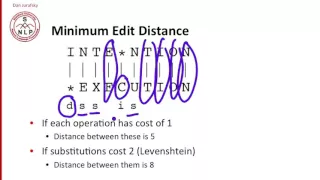
2 1 Defining Minimum Edit Distance 7 04
From playlist CS124 - Full Course
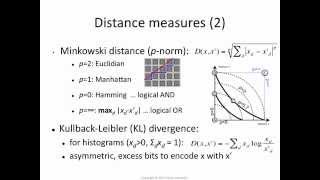
k-NN 4: which distance function?
[http://bit.ly/k-NN] The nearest-neighbour algorithm is sensitive to the choice of distance function. Euclidean distance (L2) is a common choice, but it may lead to sub-optimal performance. We discuss Minkowski (p-norm) distance functions, which generalise the Euclidean distance, and can a
From playlist Nearest Neighbour Methods

Maximum and Minimum Values (Closed interval method)
A review of techniques for finding local and absolute extremes, including an application of the closed interval method
From playlist 241Fall13Ex3

Using Bounds to Calculate Further Bounds
"Use lower and upper bounds within calculations to calculate a further lower/upper bound."
From playlist Number: Rounding & Estimation

Alberto Del Pia: Proximity in concave integer quadratic programming
A classic result by Cook, Gerards, Schrijver, and Tardos provides an upper bound of n∆ on the proximity of optimal solutions of an Integer Linear Programming problem and its standard linear relaxation. In this bound, n is the number of variables and ∆ denotes the maximum of the absolute va
From playlist Workshop: Tropical geometry and the geometry of linear programming

Lec 15 | MIT 6.451 Principles of Digital Communication II
Trellis Representations of Binary Linear Block Codes View the complete course: http://ocw.mit.edu/6-451S05 License: Creative Commons BY-NC-SA More information at http://ocw.mit.edu/terms More courses at http://ocw.mit.edu
From playlist MIT 6.451 Principles of Digital Communication II

An Introduction to Binary Code Bounds - Fernando Granha Jeronimo
A binary code is simply any subset of 0/1 strings of a fixed length. Given two strings, a standard way of defining their distance is by counting the number of positions in which they disagree. Roughly speaking, if elements of a code are sufficiently far apart, then the code is resilient to
From playlist Mathematics

Lec 7 | MIT 6.451 Principles of Digital Communication II
Introduction to Finite Fields View the complete course: http://ocw.mit.edu/6-451S05 License: Creative Commons BY-NC-SA More information at http://ocw.mit.edu/terms More courses at http://ocw.mit.edu
From playlist MIT 6.451 Principles of Digital Communication II
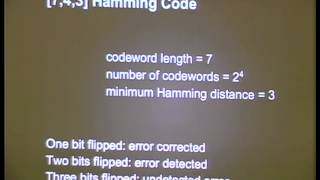
ShmooCon 2014: Unambiguous Encapsulation - Separating Data and Signaling
For more information visit: http://bit.ly/shmooc14 To download the video visit: http://bit.ly/shmooc14_down Playlist Shmoocon 2014: http://bit.ly/shmooc14_pl Speakers: Dominic Spill | Michael Ossmann Attacks against in band signaling systems have been demonstrated against Zigbee and Ether
From playlist ShmooCon 2014

Ruud Pellikaan: The coset leader weight enumerator of the code of the twisted cubic
In general the computation of the weight enumerator of a code is hard and even harder so for the coset leader weight enumerator. Generalized Reed Solomon codes are MDS, so their weight enumerators are known and its formulas depend only on the length and the dimension of the code. The coset
From playlist Combinatorics
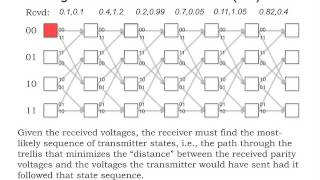
MIT 6.02 Introduction to EECS II: Digital Communication Systems, Fall 2012 View the complete course: http://ocw.mit.edu/6-02F12 Instructor: George Verghese This lecture starts with a review of encoding and decoding. The Viterbi algorithm, which includes a branch netric and a path metric,
From playlist MIT 6.02 Introduction to EECS II: Digital Communication Systems, Fall 2012

Locally testable and locally correctable codes approaching the GV bound - Shubhangi Saraf
Computer Science/Discrete Mathematics Seminar I Topic: Locally testable and locally correctable codes approaching the Gilbert-Varshamov bound Speaker: Shubhangi Sara Affiliation: Rutgers University Date: November 27, 2017 For more videos, please visit http://video.ias.edu
From playlist Mathematics

Implementing Shortest Distance - Intro to Algorithms
This video is part of an online course, Intro to Algorithms. Check out the course here: https://www.udacity.com/course/cs215.
From playlist Introduction to Algorithms

Lec 18 | MIT 6.451 Principles of Digital Communication II
Codes on Graphs View the complete course: http://ocw.mit.edu/6-451S05 License: Creative Commons BY-NC-SA More information at http://ocw.mit.edu/terms More courses at http://ocw.mit.edu
From playlist MIT 6.451 Principles of Digital Communication II

Locally Repairable Codes, Storage Capacity and Index Coding - Arya Mazumdar
Computer Science/Discrete Mathematics Seminar I Topic: Locally Repairable Codes, Storage Capacity and Index Coding Speaker: Arya Mazumdar Affiliation: University of Massachusetts, Amherst Date: Febuary 5, 2018 For more videos, please visit http://video.ias.edu
From playlist Mathematics

Bias vs Low Rank of Polynomials with...Algebraic Geometry - Abhishek Bhowmick
Let f be a polynomial of degree d in n variables over a finite field 𝔽. The polynomial is said to be unbiased if the distribution of f(x) for a uniform input x∈𝔽n is close to the uniform distribution over 𝔽, and is called biased otherwise. The polynomial is said to have low rank if it can
From playlist Mathematics

Lec 6 | MIT 6.451 Principles of Digital Communication II
Introduction to Binary Block Codes View the complete course: http://ocw.mit.edu/6-451S05 License: Creative Commons BY-NC-SA More information at http://ocw.mit.edu/terms More courses at http://ocw.mit.edu
From playlist MIT 6.451 Principles of Digital Communication II
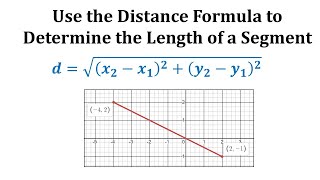
Example: Determine the Distance Between Two Points
This video shows an example of determining the length of a segment on the coordinate plane by using the distance formula. Complete Video List: http://www.mathispower4u.yolasite.com or http://www.mathispower4u.wordpress.com
From playlist Using the Distance Formula / Midpoint Formula