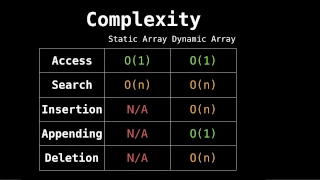
Related videos: static/dynamic arrays: https://youtu.be/PEnFFiQe1pM static/dynamic arrays code: https://youtu.be/tvw4v7FEF1w Data Structures Source Code: https://github.com/williamfiset/algorithms My website: http://www.williamfiset.com
From playlist Data structures playlist
CERIAS Security: Static source code analysis 2/6
Clip 2/6 Speaker: Jacob West · Fortify Software Creating secure code requires more than just good intentions. Programmers need to know how to make their code safe in an almost infinite number of scenarios and configurations. Static source code analysis gives users the ability to review t
From playlist The CERIAS Security Seminars 2008

CERIAS Security: Static source code analysis 4/6
Clip 4/6 Speaker: Jacob West · Fortify Software Creating secure code requires more than just good intentions. Programmers need to know how to make their code safe in an almost infinite number of scenarios and configurations. Static source code analysis gives users the ability to review t
From playlist The CERIAS Security Seminars 2008
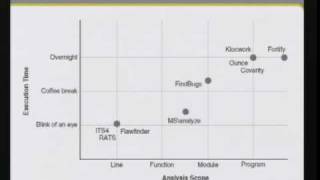
CERIAS Security: Static source code analysis 3/6
Clip 3/6 Speaker: Jacob West · Fortify Software Creating secure code requires more than just good intentions. Programmers need to know how to make their code safe in an almost infinite number of scenarios and configurations. Static source code analysis gives users the ability to review t
From playlist The CERIAS Security Seminars 2008
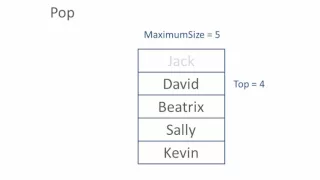
Stack Data Structure - Algorithm
This is an explanation of the dynamic data structure known as a stack. It includes an explanation of how a stack works, along with pseudocode for implementing the push and pop operations with a static array variable.
From playlist Data Structures

CERIAS Security: Static source code analysis 5/6
Clip 5/6 Speaker: Jacob West · Fortify Software Creating secure code requires more than just good intentions. Programmers need to know how to make their code safe in an almost infinite number of scenarios and configurations. Static source code analysis gives users the ability to review t
From playlist The CERIAS Security Seminars 2008

CERIAS Security: Static source code analysis 1/6
Clip 1/6 Speaker: Jacob West · Fortify Software Creating secure code requires more than just good intentions. Programmers need to know how to make their code safe in an almost infinite number of scenarios and configurations. Static source code analysis gives users the ability to review t
From playlist The CERIAS Security Seminars 2008

CERIAS Security: Static source code analysis 6/6
Clip 6/6 Speaker: Jacob West · Fortify Software Creating secure code requires more than just good intentions. Programmers need to know how to make their code safe in an almost infinite number of scenarios and configurations. Static source code analysis gives users the ability to review t
From playlist The CERIAS Security Seminars 2008

DEFCON 15: How I Learned to Stop Fuzzing and Find More Bugs
Speaker: Jacob West Manager, Security Research Group, Fortify Software Fuzzing and other runtime testing techniques are great at finding certain kinds of bugs. The trick is, effective fuzzing requires a lot of customization. The fuzzer needs to understand the protocol being spoken, antici
From playlist DEFCON 15

SOURCE Boston 2008: The CERT C++ Secure Coding Standard
Speaker: Stephen C. Dewhurst - Co-Founder and President of Semantics Consulting, Inc. An essential element of secure coding is a well documented and enforceable coding standard. Coding standards encourage programmers to follow a uniform set of rules and guidelines determined by the requir
From playlist SOURCE Boston 2008

GTAC 2015: Test Suites and Program Analysis
http://g.co/gtac Slides: https://docs.google.com/presentation/d/1yoOf_fyeN-AtQQQsTemxrranKVBUc9i-VzF_o4OqsJQ/pub Patrick Lam (University of Waterloo) Specializing static analysis techniques for test suites has yielded interesting results. We've previously learned that most tests are simp
From playlist GTAC 2015

OWASP AppSecUSA 2012: Using Interactive Static Analysis for Detection of Software Vulnerabilities
Speaker: Bill Chu We present our work of using interactive static analysis to improve upon static analysis techniques by introducing a new mixed-initiative paradigm for interacting with developers to aid in the detection and prevention of security vulnerabilities. The key difference betwe
From playlist OWASP AppSecUSA 2012
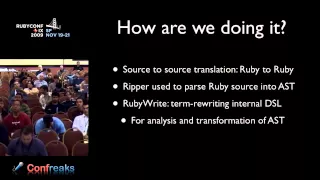
RubyConf 2009 - Using Ruby to Generate Faster Ruby Code through Partial Evaluation by: Andy Keep
Help us caption & translate this video! http://amara.org/v/GX5K/
From playlist RubyConf 2009
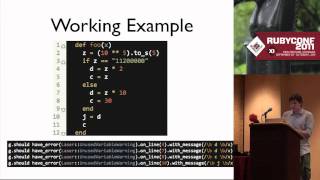
Laser: Static Analysis for Ruby, in Ruby by Michael Edgar
What truly makes Ruby special as a language is its focus on expressivity, flexibility, and dynamism. Yet these same properties - and their widespread use in the community - make even straightforward application code difficult to analyze statically in a meaningful way. Laser seeks to change
From playlist Ruby Conference 2011
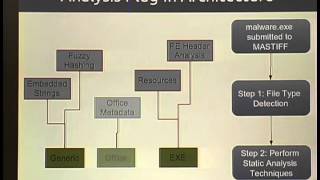
ShmooCon 2013: astiff: Automated Static Analysis Framework
For more information and to download the video visit: http://bit.ly/shmoocon2013 Playlist ShmooCon 2013: http://bit.ly/Shmoo13 Speaker: Tyler Hudak Malware analysis consists of two phases -- static and dynamic analysis. Dynamic analysis, or analyzing the behavior of a sample, has already
From playlist ShmooCon 2013
