
Cryptographic Hash Functions: Part 1
Cryptographic Hash Functions Applications of Crypto Hash Functions Birthday Problem Secure Hash Algorithm (SHA)
From playlist Network Security

Cryptographic Hash Functions: Part 2
Cryptographic Hash Functions Applications of Crypto Hash Functions Birthday Problem Secure Hash Algorithm (SHA)
From playlist Network Security

An informal introduction to cryptography. Part of a larger series teaching programming at http://codeschool.org
From playlist Cryptography

Hash Tables and Hash Functions
This computer science video describes the fundamental principles of the hash table data structure which allows for very fast insertion and retrieval of data. It covers commonly used hash algorithms for numeric and alphanumeric keys and summarises the objectives of a good hash function. Co
From playlist Data Structures

https://en.wikipedia.org/wiki/SHA-1#Examples_and_pseudocode If you have any questions of want to contribute to code or videos, feel free to write me a message on youtube or get my contact in the About section or googling my contacts.
From playlist Programming

From playlist Cryptography Lectures
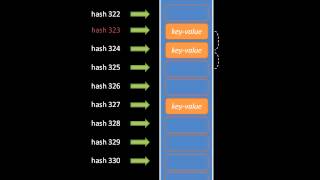
Introductory coverage of fundamental data structures. Part of a larger series teaching programming. Visit http://codeschool.org
From playlist Data Structures

*** This is CS50, Harvard University's introduction to the intellectual enterprises of computer science and the art of programming. *** HOW TO SUBSCRIBE http://www.youtube.com/subscription_center?add_user=cs50tv HOW TO TAKE CS50 edX: https://cs50.edx.org/ Harvard Extension School: ht
From playlist CS50 Shorts
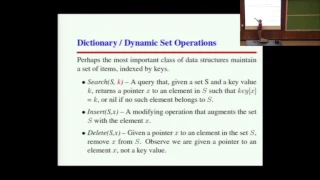
This is Lecture 6 of the CSE373 (Analysis of Algorithms) course taught by Professor Steven Skiena [http://www3.cs.stonybrook.edu/~skiena/] at Stony Brook University in 2016. The lecture slides are available at: https://www.cs.stonybrook.edu/~skiena/373/newlectures/lecture6.pdf More infor
From playlist CSE373 - Analysis of Algorithms 2016 SBU

*** This is CS50, Harvard University's introduction to the intellectual enterprises of computer science and the art of programming. *** HOW TO SUBSCRIBE http://www.youtube.com/subscription_center?add_user=cs50tv HOW TO TAKE CS50 edX: https://cs50.edx.org/ Harvard Extension School: ht
From playlist CS50 Walkthroughs 2019

From playlist CS50 Walkthroughs 2012
HashDB - Malware API Hashing Obfuscation Solved Forever (Not Clickbait)
Join us for the release of HashDB a free community-source solution to malware API hashing! Expand for more... ----- OALABS DISCORD https://discord.gg/6h5Bh5AMDU OALABS PATREON https://www.patreon.com/oalabs OALABS TIP JAR https://ko-fi.com/oalabs OALABS GITHUB https://github.com/OALabs
From playlist Open Analysis Live!

CSE 373 --- Lecture 6: Hashing (Fall 2021)
9/9/21
From playlist CSE373 --- Analysis of Algorithms (Fall 2021)

From playlist Cryptography Lectures




