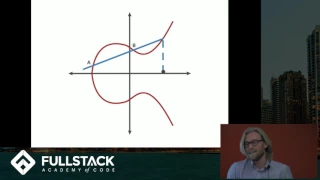
Elliptic Curve Cryptography Tutorial - Understanding ECC through the Diffie-Hellman Key Exchange
Learn more advanced front-end and full-stack development at: https://www.fullstackacademy.com Elliptic Curve Cryptography (ECC) is a type of public key cryptography that relies on the math of both elliptic curves as well as number theory. This technique can be used to create smaller, fast
From playlist Elliptic Curves - Number Theory and Applications
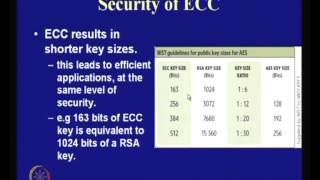
Application of Elliptic Curves to Cryptography
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security
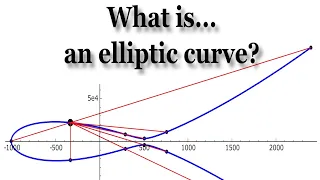
In this talk, we will define elliptic curves and, more importantly, we will try to motivate why they are central to modern number theory. Elliptic curves are ubiquitous not only in number theory, but also in algebraic geometry, complex analysis, cryptography, physics, and beyond. They were
From playlist An Introduction to the Arithmetic of Elliptic Curves
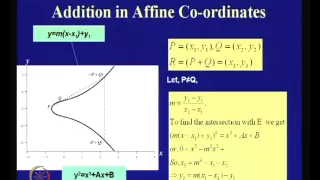
An Introduction to Elliptic Curve Cryptography
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Elliptic Curve Cryptography and Applications
At the SIAM Annual Meeting held in Minneapolis in July, Dr. Kristin Lauter of Microsoft Research discussed Elliptic Curve Cryptography as a mainstream primitive for cryptographic protocols and applications. The talk surveyed elliptic curve cryptography and its applications, including appli
From playlist What is math used for?

Elliptic Curve ElGamal Cryptosystem
In this video I primarily do through the Elliptic Curve ElGamal crytposystem (Bob's variables/computations, Alice's variables/computations, what is sent, and how it is decrypted by Bob). In addition, I go over the basics of elliptic curves such as their advantages and how they are written.
From playlist Cryptography and Coding Theory

For more cryptography, subscribe @JeffSuzukiPolymath
From playlist Elliptic Curves - Number Theory and Applications

Implementation of Elliptic Curve Cryptography
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

The Elliptic Curve Digital Signature Algorithm and raw transactions on Bitcoin
https://en.wikipedia.org/wiki/Elliptic_Curve_Digital_Signature_Algorithm https://hackernoon.com/what-is-the-math-behind-elliptic-curve-cryptography-f61b25253da3 https://en.wikipedia.org/wiki/Elliptic_curve https://en.bitcoin.it/wiki/Secp256k1 http://www.ijsrp.org/research-paper-1117/ij
From playlist Programming

Mathematics in Post-Quantum Cryptography - Kristin Lauter
2018 Program for Women and Mathematics Topic: Mathematics in Post-Quantum Cryptography Speaker: Kristin Lauter Affiliation: Microsoft Research Date: May 21, 2018 For more videos, please visit http://video.ias.edu
From playlist My Collaborators

Elliptic Curve Arithmetic and Bitcoin | Nathan Dalaklis
Bitcoin is a cryptocurrency that uses elliptic curves in the ECDSA. Since cryptosystems often require some form of arithmetic to encode and decode information we have a couple questions to ask; What are elliptic curves? And how can we do arithmetic on an elliptic curve? ________ Standards
From playlist The New CHALKboard

Craig Costello - Post-quantum key exchange from supersingular isogenies- IPAM at UCLA
Recorded 26 July 2022. Craig Costello of Microsoft Research presents "Post-quantum key exchange from supersingular isogenies" at IPAM's Graduate Summer School Post-quantum and Quantum Cryptography. Abstract: This talk will give an overview of Supersingular isogeny Diffie-Hellman (SIDH): t
From playlist 2022 Graduate Summer School on Post-quantum and Quantum Cryptography

Elliptic Curves: Good books to get started
A few books for getting started in the subject of Elliptic Curves, each with a different perspective. I give detailed overviews and my personal take on each book. 0:00 Intro 0:41 McKean and Moll, Elliptic Curves: Function Theory, Geometry, Arithmetic 10:14 Silverman, The Arithmetic of El
From playlist Math

Kritin Lauter, Supersingular isogeny graphs in cryptography
VaNTAGe Seminar, September 20, 2022 License: CC-BY-NC-SA Some of the papers mentioned in this talk: Charles, Goren, Lauter 2007: https://doi.org/10.1007/s00145-007-9002-x Mackenzie 2008: https://doi.org/10.1126/science.319.5869.1481 Pizer 1990: https://doi.org/10.1090/S0273-0979-1990-15
From playlist New developments in isogeny-based cryptography

Elliptic Curves - Lecture 6a - Ramification (continued)
This video is part of a graduate course on elliptic curves that I taught at UConn in Spring 2021. The course is an introduction to the theory of elliptic curves. More information about the course can be found at the course website: https://alozano.clas.uconn.edu/math5020-elliptic-curves/
From playlist An Introduction to the Arithmetic of Elliptic Curves

Mathematics in Cryptography II - Toni Bluher
2018 Program for Women and Mathematics Topic: Mathematics in Cryptography II Speaker: Toni Bluher Affiliation: National Security Agency Date: May 21, 2018 For more videos, please visit http://video.ias.edu
From playlist Mathematics