
From playlist everything

What is a Bézier curve? Programmers use them everyday for graphic design, animation timing, SVG, and more. #shorts #animation #programming Animated Bézier https://www.jasondavies.com/animated-bezier/
From playlist CS101

RustConf 2017 - Fast, Safe, Pure-Rust Elliptic Curve Cryptography
Fast, Safe, Pure-Rust Elliptic Curve Cryptography by Isis Lovecruft & Henry De Valence This talk discusses the design and implementation of curve25519-dalek, a pure-Rust implementation of operations on the elliptic curve known as Curve25519. We will discuss the goals of the library and g
From playlist RustConf 2017

RustConf 2017 - Fast, Safe, Pure-Rust Elliptic Curve Cryptography
Fast, Safe, Pure-Rust Elliptic Curve Cryptography by Isis Lovecruft & Henry De Valence This talk discusses the design and implementation of curve25519-dalek, a pure-Rust implementation of operations on the elliptic curve known as Curve25519. We will discuss the goals of the library and gi
From playlist RustConf 2017

CERIAS Security: Sphinx: A Compact and Provably Secure Mix Format 4/6
Clip 4/6 Speaker: Ian Goldberg · University of Waterloo Mix networks, originally proposed in 1981, provide a way for Internet users to send messages--such as email, blog posts, or tweets--without automatically revealing their identities or their locations. In this talk, we will describe
From playlist The CERIAS Security Seminars 2009

《康熙好經典》康熙好經典YouTube網路頻道 ●更多精彩內容歡迎點閱以下網址 節目網路頻道:https://www.youtube.com/channel/UC8mAFu8AQNdJfiBS33qWvTA 中天綜藝攏底家:https://www.facebook.com/36tvshow 《康熙來了》 :https://www.youtube.com/playlist?list=PLD97A53B76747131E 《大學生了沒》:https://www.youtube.com/playlist?list=PL1EACA2F821AA5074 《SS小燕之夜》:http
From playlist Everyday How-to

Ruby Conf 2013 - Being Boring: A Survival Guide to Ruby Cryptography
We all know that security is hard, and that math is hard, but what happens when you put them together? Cryptography is an increasingly essential tool for building secure systems, but also a perilous minefield where any number of mistakes can lead to insecure systems. This talk will take y
From playlist Ruby Conf 2013 - Miami Beach, FL

MountainWest Devops 2014 - Bridging the DevOps Islands with Pantry
By Jason Roelofs DevOps is a fascinating, quickly growing field. With Chef, Puppet, Ansible, Salt, Packer, Docker, Vagrant, AWS, and others, there are many ways to get an infrastructure up and running. However, it is quickly evident to those entering this field that choosing one tool ofte
From playlist MountainWest DevOps 2014

Kernel Recipes 2015 - WireGuard: A Kernelspace VPN - by J. A. Donenfeld
WireGuard is an upcoming project to replace IPSec with a newer more modern and secure VPN protocol. It lives inside the kernel and provides a very simple and novel interface for setting up secure encrypted network tunnels. All the cryptography is cutting edge -- DJB's Curve25519, ChaCha20,
From playlist Kernel Recipes 2015

查看本系列视频中的其他几个视频: Part 1 – 导入数据: https://youtu.be/lyaIDHyOlFc Part 2 – 预处理数据: https://youtu.be/ais_Oj6Fx-E Part 3 – 分析数据: https://youtu.be/I1EQx3O2qCk Part 4 -可视化数据: https://youtu.be/rLeMOEWkoa8 Part 5 – 模型预测: https://youtu.be/BBtnVjVYI2k Part 6 – 大数据扩展: https://youtu.be/xGzMMkFURb8 Part 7
From playlist MATLAB 数据科学系列视频

查看本系列视频中的其他几个视频: Part 1 – 导入数据: https://youtu.be/lyaIDHyOlFc Part 2 – 预处理数据: https://youtu.be/ais_Oj6Fx-E Part 3 – 分析数据: https://youtu.be/I1EQx3O2qCk Part 4 -可视化数据: https://youtu.be/rLeMOEWkoa8 Part 5 – 模型预测: https://youtu.be/BBtnVjVYI2k Part 6 – 大数据扩展: https://youtu.be/xGzMMkFURb8 Part 7
From playlist MATLAB 数据科学系列视频

工程师谈强化学习 Part 5 | 克服强化学习中的实际问题
查看本系列视频中的其他几个视频: Part 2 - 了解环境与奖励: https://youtu.be/0ODB_DvMiDI Part 3 - 策略和学习算法: https://youtu.be/7cF3VzP5EDI Part 4 - 行走机器人示例: https://youtu.be/Wypc1a-1ZYA Part 5 -克服强化学习中的实际问题: https://youtu.be/zHV3UcH-nr0 在这段视频中,我将解决一些不太容易注意到的进入生产部署环节的强化学习问题,并尝试提供一些方法来缓和这些问题。即使没有直接的方法来解决你将面临的一些挑战,至少
From playlist 强化学习

查看本系列视频中的其他几个视频: Part 2 - 了解环境与奖励: https://youtu.be/0ODB_DvMiDI Part 3 - 策略和学习算法: https://youtu.be/7cF3VzP5EDI Part 4 - 行走机器人示例: https://youtu.be/Wypc1a-1ZYA Part 5 -克服强化学习中的实际问题: https://youtu.be/zHV3UcH-nr0 在本视频中,我们将介绍基于智能体的算法函数。我们将探讨为什么要用神经网络来表示函数,为什么要建立两个神经网络,以及它们在强大的称为“执行器一评价器”的系列方
From playlist 强化学习

Stanford Seminar - Building a Trustworthy Business in the Post-Snowden Era
"Building a Trustworthy Business in the Post-Snowden Era" -Alex Stamos, Artemis Internet Colloquium on Computer Systems Seminar Series (EE380) presents the current research in design, implementation, analysis, and use of computer systems. Topics range from integrated circuits to operatin
From playlist Engineering
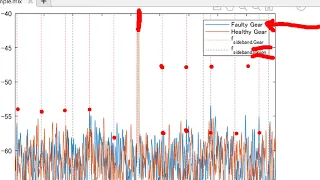
予知保全・異常検知の例として、以下の二つの例をご紹介します。 1. ギアの故障診断 2. 心拍の異常・正常判定 - LSTMネットワークによるECG信号の分類: https://bit.ly/2IBzlZ9 - 機械学習のための信号処理: http://bit.ly/2E9Z2fZ - MATLABで信号処理~各種センサー信号を題材として~: http://bit.ly/2E96tnx - MATLABで信号処理~各種フィルタ設計を題材として~ : http://bit.ly/2E7nNJx ----------------------------------
From playlist 予知保全のための信号処理ビデオシリーズ

