
Prealgebra Lecture 3.4 Part 2: Translating Sentences Into Equations
From playlist Prealgebra Playlist 1

Prealgebra Lecture 2.2 Part 1: Adding Integers
From playlist Prealgebra Playlist 1

From playlist Cryptography Lectures

NOTACON 2: Recent Attacks Against Hash Functions
Speaker: Matthew Fanto In recent months, a large amount of research into the security of cryptographic hash functions has revealed serious flaws in every widely used hash function, including MD4, MD5, RIPEMD, HAVAL, SHA-0, and SHA-1. These flaws have far reaching consequences, as hash fun
From playlist Notacon 2

Clip 5/7 Speaker: Dan Kaminsky For more information go to: http://events.ccc.de/congress/2009/Fahrplan/events/3658.en.html
From playlist 26C3: Here be dragons day 3
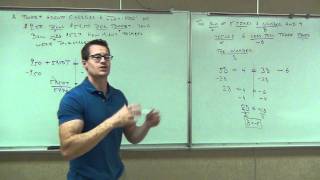
Prealgebra Lecture 3.4 Part 3: Translating Sentences Into Equations
From playlist Prealgebra Playlist 1

1. Signatures, Hashing, Hash Chains, e-cash, and Motivation
MIT MAS.S62 Cryptocurrency Engineering and Design, Spring 2018 Instructor: Neha Narula, Tadge Dryja View the complete course: https://ocw.mit.edu/MAS-S62S18 YouTube Playlist: https://www.youtube.com/playlist?list=PLUl4u3cNGP61KHzhg3JIJdK08JLSlcLId Introduces currency, banking, and electro
From playlist MIT MAS.S62 Cryptocurrency Engineering and Design, Spring 2018

Prealgebra Lecture 4.3: How to Multiply and Divide Fractions
https://www.patreon.com/ProfessorLeonard Prealgebra Lecture 4.3: Multiplying and Dividing Fractions
From playlist Prealgebra (Full Length Videos)

Prealgebra Lecture 2.2 Part 2: Adding Integers
From playlist Prealgebra Playlist 1

Mathematics in Post-Quantum Cryptography - Kristin Lauter
2018 Program for Women and Mathematics Topic: Mathematics in Post-Quantum Cryptography Speaker: Kristin Lauter Affiliation: Microsoft Research Date: May 21, 2018 For more videos, please visit http://video.ias.edu
From playlist My Collaborators
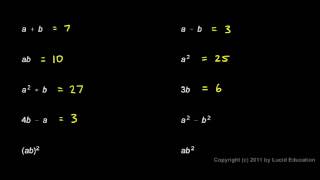
Prealgebra 2.07b - Evaluating Expressions
Evaluating expressions for given values of the variables. From the Prealgebra course by Derek Owens. This course is available online at http://www.LucidEducation.com.
From playlist Prealgebra Chapter 2 (Complete chapter)

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security
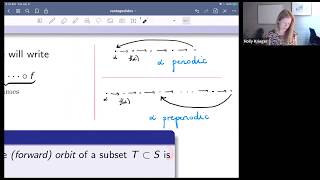
Holly Krieger, Equidistribution and unlikely intersections in arithmetic dynamics
VaNTAGe seminar on May 26, 2020. License: CC-BY-NC-SA. Closed captions provided by Marley Young.
From playlist Arithmetic dynamics

Prealgebra Lecture 2.5 Part 7: Order of Operations with Integers
From playlist Prealgebra Playlist 1
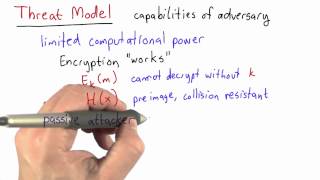
Threat Model - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Prealgebra Lecture 1.2 Part 1: Place Value and Expanded Form
From playlist Prealgebra Playlist 1
Math 101 Fall 2017 112717 Open Sets and Continuity
Definitions: open set, closed set; examples. Statement of DeMorgan's Laws. Definition: pre-image. Example. Theorem: f is continuous iff the preimage of any open set is open. Motivation for compact sets.
From playlist Course 6: Introduction to Analysis (Fall 2017)

Prealgebra Lecture 4.1 Part 3: Introduction to Fractions
From playlist Prealgebra Playlist 1

Prealgebra Lecture 4.1 Part 1: Introduction to Fractions
From playlist Prealgebra Playlist 1

Preimage and kernel example | Matrix transformations | Linear Algebra | Khan Academy
Example involving the preimage of a set under a transformation. Definition of kernel of a transformation. Watch the next lesson: https://www.khanacademy.org/math/linear-algebra/matrix_transformations/linear_transformations/v/sums-and-scalar-multiples-of-linear-transformations?utm_source=Y
From playlist Matrix transformations | Linear Algebra | Khan Academy