
One Time Pad - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Bitwise Operators 2: The OR Operation
This computer science video describes the bitwise operation OR. It explains how the OR operation works with unsigned integers and how the OR operation can be used with a bitmask to manipulate the contents of a register containing bit flags. The equivalent OR operators are demonstrated i
From playlist Bitwise Operators

Symmetric Key Cryptography | Stream Cipher & Block Cipher Explained | Network Security | Simplilearn
This video on Symmetric Key Cryptography will acquaint you with the process of symmetric encryption and decryption. Here, we take a small recap into cryptography, the working and applications of symmetric key cryptography, and its advantages. We also have stream cipher and block cipher exp
From playlist Cyber Security Playlist [2023 Updated]🔥

An introduction to the 16-byte by 8-bit static RAM that we're going to build for our 8-bit computer. Support me on Patreon: https://www.patreon.com/beneater Previously we built a 1-bit register: https://youtu.be/-arYx_oVIj8 Next we extended that to build an 8-bit register: https://youtu
From playlist Building an 8-bit breadboard computer!

Secret Sharing Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

The Trick That Solves Rubik’s Cubes and Breaks Ciphers (Meet in the Middle)
What do the Rubik's cube and a cipher from the 70s have in common? Let's find out. 0:00 Rubik's cube 9:40 DES ------------------------ Links: Feliks setting the 4.73 record https://www.youtube.com/watch?v=R07JiT0PlcE&ab_channel=FeliksZemdegs webpage "God's number is 20" http://www.cub
From playlist Algorithms

OHM2013: SIM card exploitation
For more information visit: http://bit.ly/OHM13_web To download the video visit: http://bit.ly/OHM13_down Playlist OHM 2013: http://bit.ly/OHM13_pl Speaker: Karsten Nohl SIM cards are among the most widely-deployed computing platforms with over 7 billion cards in active use, but little i
From playlist OHM 2013

Early Unix Implementation - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

How secure is 256 bit security?
How hard is it to find a 256-bit hash just by guessing and checking? Help fund future projects: https://www.patreon.com/3blue1brown An equally valuable form of support is to simply share some of the videos. Home page: https://www.3blue1brown.com/ Several people have commented about how 2^
From playlist Shorter videos

Small M - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security
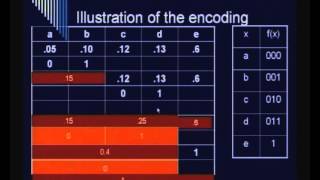
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Rsa Encryption Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

An informal introduction to cryptography. Part of a larger series teaching programming at http://codeschool.org
From playlist Cryptography

DEFCON 20: Defeating PPTP VPNs and WPA2 Enterprise with MS-CHAPv2
Speakers: MOXIE MARLINSPIKE | DAVID HULTON | MARSH RAY MS-CHAPv2 is an authentication and key negotiation protocol that, while old and battered, is still unfortunately deployed quite widely. It underpins almost all PPTP VPN services, and is relied upon by many WPA2 Enterprise wireless dep
From playlist DEFCON 20

RailsConf 2018: Encrypted Credentials on Rails 5.2: Secrets to Success by Christopher Rigor
RailsConf 2018: Encrypted Credentials on Rails 5.2: Secrets to Success by Christopher Rigor Secrets are out. Credentials are in. This new Rails 5.2 feature offers a number of advantages over the old way of managing secrets. You get atomic deploys, you avoid putting sensitive data on envir
From playlist RailsConf 2018

Symmetric Key Cryptography: Cryptographic Techniques
This is the fifth in a series about cryptography; an extremely important aspect of computer science and cyber security. It reviews how the XOR logical operation can be used to encrypt at the bit level in symmetric key cryptography, then shows how this can be combined with permutation step
From playlist Cryptography

Cryptography: Caesar Cipher With Shift
This lesson explains how to encrypt and decrypt a message using Caeser cipher with a shift. Site: http://mathispower4u.com
From playlist Cryptography

