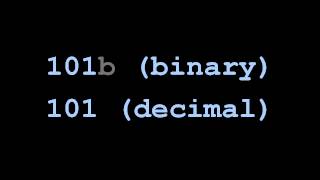
512-bit computing
In computer architecture, 512-bit integers, memory addresses, or other data units are those that are 512 bits (64 octets) wide. Also, 512-bit central processing unit (CPU) and arithmetic logic unit (ALU) architectures are those that are based on registers, address buses, or data buses of that size.There are currently no mainstream general-purpose processors built to operate on 512-bit integers or addresses, though a number of processors do operate on 512-bit data. (Wikipedia).