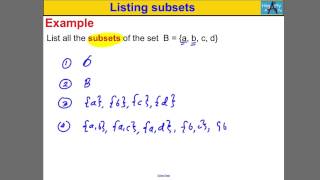
This video defines and give the notation used for subsets and proper subsets. http://mathispower4u.com
From playlist Sets

Introduction to Subsets (new version available)
This video defines and give the notation used for subsets and proper subsets. https://youtu.be/mqBDYTcpAA0 The new version fixed an error in the audio.
From playlist Set Theory

In this exercise problem we prove that the intersection of a set with the union of two other sets, is equal to the union of the intersection of the first and the second and the first and the third sets.
From playlist Abstract algebra

Find the Intersections and Union of Three Sets as Lists
This video explains how to determine the union and intersection of three sets. http://mathispower4u.com
From playlist Sets
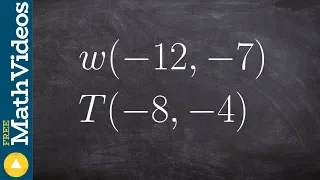
Find the midpoint between two points w(–12,–7), T(–8,–4)
👉 Learn how to find the midpoint between two points. The midpoint between two points is the point halfway the line joining two given points in the coordinate plane. To find the midpoint between two points we add the x-coordinates of the two given points and divide the result by 2. This giv
From playlist Points Lines and Planes

Determine if the Subset of Vectors (a,b,1) is a Subspace in R3
This video explains how to determine if a subset is a subspace of a vector space.
From playlist Spanning Sets and Subspaces

On the Ramanujan Conjecture in Geometric Langlands by Dario Beraldo
Program Quantum Fields, Geometry and Representation Theory 2021 (ONLINE) ORGANIZERS: Aswin Balasubramanian (Rutgers University, USA), Indranil Biswas (TIFR, india), Jacques Distler (The University of Texas at Austin, USA), Chris Elliott (University of Massachusetts, USA) and Pranav Pandi
From playlist Quantum Fields, Geometry and Representation Theory 2021 (ONLINE)

CERIAS Security: Database Assurance: Anomaly Detection for Relational Databases 3/5
Clip 3/5 Speaker: Peter Mork Behind countless complex applications lurk trusty relational databases that are responsible for managing the data that fuel these applications. For example, relational databases are used to support electronic medical health record systems, timecard reporting
From playlist The CERIAS Security Seminars 2009

Cuban Missile Crisis | The 20th century | World history | Khan Academy
Sal gives an overview of the Cuban Missile Crisis. Created by Sal Khan. Watch the next lesson: https://www.khanacademy.org/humanities/world-history/euro-hist/cold-war/v/vietnam-war?utm_source=YT&utm_medium=Desc&utm_campaign=worldhistory Missed the previous lesson? https://www.khanacademy
From playlist Period 8: 1945-1980 | AP US History | Khan Academy

Determine if the Subset of Vectors (a,b,0) is a Subspace in R3
This video explains how to determine if a subset is a subspace of a vector space.
From playlist Spanning Sets and Subspaces

Cybersecurity Career outlook 2020 | Cybersecurity Jobs, Skills,Roles| Edureka Ethical Hacking Live-3
🔥Edureka Online Training: https://www.edureka.co/cybersecurity-certification-training This Edureka LIVE session will give you an insight into why Cyber Security is considered to be a lucrative domain in the IT industry. You will also understand why Cyber Security & Ethical Hacking professi
From playlist Edureka Live Classes 2020

attack-driven defense - zane lackey
Traditionally, defense has been approached without enough emphasis on countering real world attack behaviors. This presentation will cover new network defense techniques from an attack perspective, specifically focusing on building detection systems around initial compromise, persistence/C
From playlist AppSec California 2014
Global surfaces of section for Reeb flows – P. Salomão & U. Hryniewicz – ICM2018
Geometry Invited Lecture 5.4 Global surfaces of section for Reeb flows in dimension three and beyond Pedro Salomão & Umberto Hryniewicz Abstract: We survey some recent developments in the quest for global surfaces of section for Reeb flows in dimension three using methods from Symplectic
From playlist Geometry

Michal Pilipczuk: Tight Complexity Lower Bounds for Integer Linear Programming with Few Constraints
We show that verifying feasibility of ILP instances of the form fAx = b; x 0g where A has m rows (constraints) and coecients in f1; 0; 1g cannot be done in time 2 to the power of o(m log m) * n to the power of O(1) assuming the Exponential Time Hypothesis. This shows that the running tim
From playlist Workshop: Parametrized complexity and discrete optimization

Extremal Combinatorics with Po-Shen Loh 04/03 Fri
Carnegie Mellon University is protecting the community from the COVID-19 pandemic by running courses online for the Spring 2020 semester. This is the video stream for Po-Shen Loh’s PhD-level course 21-738 Extremal Combinatorics. Professor Loh will not be able to respond to questions or com
From playlist CMU PhD-Level Course 21-738 Extremal Combinatorics

Additive number theory: Extremal problems and the combinatorics of sum. (Lecture 4) by M. Nathanson
Program Workshop on Additive Combinatorics ORGANIZERS: S. D. Adhikari and D. S. Ramana DATE: 24 February 2020 to 06 March 2020 VENUE: Madhava Lecture Hall, ICTS Bangalore Additive combinatorics is an active branch of mathematics that interfaces with combinatorics, number theory, ergod
From playlist Workshop on Additive Combinatorics 2020