Stanford Seminar - The TLS 1.3 Protocol
"The TLS 1.3 Protocol" - Eric Rescorla of Mozilla and RTFM, Inc. About the talk: Transport Layer Security (TLS) is used for securing everything from Web transactions (HTTPS) to voice and video calls (DTLS-SRTP). However, the basic design of TLS dates back to the mid 1990s and the protocol
From playlist Engineering

System of Equations with Three Equations and Three Variables
Please Subscribe here, thank you!!! https://goo.gl/JQ8Nys System of Equations with Three Equations and Three Variables
From playlist Systems of Equations

Low Pass Filters & High Pass Filters : Data Science Concepts
What is a low pass filter? What is a high pass filter? Sobel Filter: https://en.wikipedia.org/wiki/Sobel_operator
From playlist Time Series Analysis
A10 Example problem of multiplicity three
An example problem of multiplicity three.
From playlist A Second Course in Differential Equations
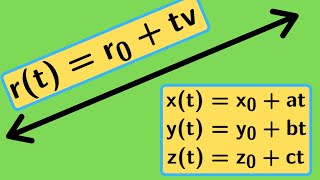
Multivariable Calculus | Three equations for a line.
We present three equations that represent the same line in three dimensions: the vector equation, the parametric equations, and the symmetric equation. http://www.michael-penn.net http://www.randolphcollege.edu/mathematics/
From playlist Lines and Planes in Three Dimensions

An intro to the core protocols of the Internet, including IPv4, TCP, UDP, and HTTP. Part of a larger series teaching programming. See codeschool.org
From playlist The Internet

How do you send a secret message if someone might be eavesdropping? How can you give someone a locked box to open without giving them the key? Here, we take a look at the three-pass protocol and man-in-the-middle attacks. 0:00 Locks and Keys 1:20 Three-Pass Protocol 3:28 Man in the Middle
From playlist Spanning Tree Favorites

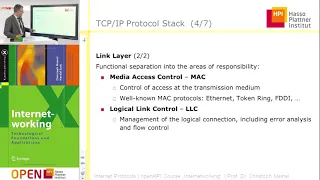
23C3: Design and Implementation of an object-oriented, secure TCP/IP Stack
Speakers: Andreas Bogk, Hannes Mehnert Ethereal^W Wireshark without remote exploits - a proof of concept We present a domain-specific language (DSL) capable to describe ad-hoc defined protocols like TCP/IP. Additionally we developed other libraries, like a flow graph for packet proce
From playlist 23C3: Who can you trust

ElixirConf 2016 - Implementing Binary Protocols with Elixir by Ole Michaelis
Implementing Binary Protocols with Elixir by Ole Michaelis Binary protocols are all around us, HTTP/2, HPACK, or DNS are only a few examples. Pretty efficient on the transport layer they reduce size dramatically and enable a set of great features. But they are often more complex to implem
From playlist ElixirConf 2016

DEFCON 15: Functional Fuzzing with Funk
Speaker: Benjamin Kurtz This talk will introduce a simple and incredibly powerful framework for the scripted generation of network traffic: Funk, a new tool for fuzzing arbitrary network protocols written using the Chicken Scheme-to-C compiler. Source code will be provided and explained,
From playlist DEFCON 15

Communications and Network Security | CISSP Training Videos
🔥 Enroll for FREE CISSP Course & Get your Completion Certificate: https://www.simplilearn.com/learn-cloud-security-basics-skillup?utm_campaign=CCSP&utm_medium=DescriptionFirstFold&utm_source=youtube Communication and Network Security : Domain 4 of the CISSP certification course offered by
From playlist Cyber Security Playlist [2023 Updated]🔥

DEFCON 16: Nail the Coffin Shut, NTLM is Dead
Speaker: Kurt Grutzmacher, Security Researcher Ever since SirDystic's SMBRelay release the weaknesses of the NTLM protocol have been repeatedly shown. For over twenty years this protocol has been refined by Microsoft, it's time to let it go and stop supporting it within our networks. Thi
From playlist DEFCON 16

Lecture 6 of Stanford’s CS193p SwiftUI development course given during the Spring of 2021 finished off the discussion of the Swift Type System with an explanation of perhaps the most important kind of type in Swift: protocols. We touch on a number of protocol concepts, including a "constra
From playlist CS193P Spring 2021

The nightmare future humanity avoided
The Montreal Protocol was designed to save the ozone layer, but it may have ended up saving the planet. Learn more about how the atmosphere absorbs radiation with Brilliant! https://www.brilliant.org/simonclark A new paper this year examined the "world avoided" via the Montreal Protocol,
From playlist Science videos

Network Security Tutorial For Beginners | Cybersecurity Training | Edureka | Cybersecurity Live - 3
🔥Edureka Cyber Security Course: https://www.edureka.co/cybersecurity-certification-training This Edureka video gives an introduction to Network Security and its nuances. It discusses the need of network security, tools for network security and various other fundamental concepts. 🔴Subscri
From playlist Edureka Live Classes 2020
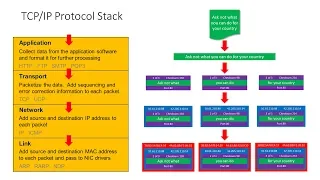
Computer Networks. Part Six: The TCP/IP Protocol Stack and Routers
This is the sixth in a series about computer networks. This video describes the role of a network protocol, and specifically details the TCP/IP suite of protocols. The need for a layered approach to networking software is discussed including the four layer TCP/IP stack and the relevance
From playlist Computer Networks

Firewalls and Intrusion Detection Systems
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security