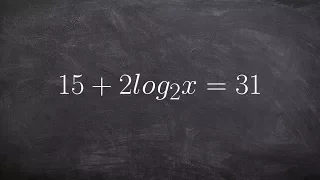Critical phenomena | Graph theory | Cellular automata
The Mathematics of Chip-Firing
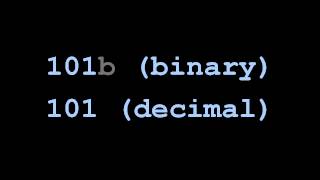
The Mathematics of Chip-Firing is a textbook in mathematics on chip-firing games and abelian sandpile models. It was written by Caroline Klivans, and published in 2018 by the CRC Press. (Wikipedia).