
Symmetric matrices - eigenvalues & eigenvectors
Free ebook http://tinyurl.com/EngMathYT A basic introduction to symmetric matrices and their properties, including eigenvalues and eigenvectors. Several examples are presented to illustrate the ideas. Symmetric matrices enjoy interesting applications to quadratic forms.
From playlist Engineering Mathematics

The Symmetric Difference is Associative Proof Video
Please Subscribe here, thank you!!! https://goo.gl/JQ8Nys The Symmetric Difference is Associative Proof Video. This is video 3 on Binary Operations.
From playlist Abstract Algebra

Symmetric Cryptosystems - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Symmetric Groups (Abstract Algebra)
Symmetric groups are some of the most essential types of finite groups. A symmetric group is the group of permutations on a set. The group of permutations on a set of n-elements is denoted S_n. Symmetric groups capture the history of abstract algebra, provide a wide range of examples in
From playlist Abstract Algebra
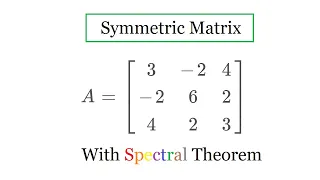
Diagonalizing a symmetric matrix. Orthogonal diagonalization. Finding D and P such that A = PDPT. Finding the spectral decomposition of a matrix. Featuring the Spectral Theorem Check out my Symmetric Matrices playlist: https://www.youtube.com/watch?v=MyziVYheXf8&list=PLJb1qAQIrmmD8boOz9a8
From playlist Symmetric Matrices

In this video we construct a symmetric group from the set that contains the six permutations of a 3 element group under composition of mappings as our binary operation. The specifics topics in this video include: permutations, sets, groups, injective, surjective, bijective mappings, onto
From playlist Abstract algebra

7. Decision Problems for Automata and Grammars
MIT 18.404J Theory of Computation, Fall 2020 Instructor: Michael Sipser View the complete course: https://ocw.mit.edu/18-404JF20 YouTube Playlist: https://www.youtube.com/playlist?list=PLUl4u3cNGP60_JNv2MmK3wkOt9syvfQWY Quickly reviewed last lecture. Showed the decidability of various pro
From playlist MIT 18.404J Theory of Computation, Fall 2020

Symmetric and skew symmetric matricies (Ch5 Pr15)
Here we show that A+A^T and AA^T are symmetric matrices, and A-A^T is skew symmetric for A is a square matrix. Presented by N J Wildberger of the School of Mathematics and Statistics, Faculty of Science, UNSW.
From playlist Mathematics 1A (Algebra)

Cryptography - Seminar 5 - Polynomial time
This seminar series is about the mathematical foundations of cryptography. In this seminar Eleanor McMurtry explains the definition of probabilistic polynomial time interactive Turing machines. The webpage for this seminar is https://lnor.net/uc-seminar.html. You can join this seminar fr
From playlist Metauni

Nathalie Aubrun: About the Domino problem on finitely generated groups - Lecture 1
Abstract: Subshifts of finite type are of high interest from a computational point of view, since they can be described by a finite amount of information - a set of forbidden patterns that defines the subshift - and thus decidability and algorithmic questions can be addressed. Given an SFT
From playlist Mathematical Aspects of Computer Science

Summary - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Wolfram Physics III: Completion Procedures and Basic Quantum Mechanics"
Find more information about the summer school here: https://education.wolfram.com/summer/school Stay up-to-date on this project by visiting our website: http://wolfr.am/physics Check out the announcement post: http://wolfr.am/physics-announcement Find the tools to build a universe: https:
From playlist Wolfram Summer Programs

Wolfram Physics Project: Working Session Wednesday, Apr. 29, 2020 [Finding Black Hole Structures]
Stephen Wolfram & Jonathan Gorard continue answering questions about the new Wolfram Physics Project, this time for a working session on finding structures of blackholes using the Wolfram Model. Begins at 1:36 Originally livestreamed at: https://twitch.tv/stephen_wolfram Stay up-to-date
From playlist Wolfram Physics Project Livestream Archive

Wolfram Physics Project: Working Session Tuesday, May 26, 2020 [Rulial Space and Other Topics]
This is a Wolfram Physics Project working session on Rulial space and other topics in the Wolfram Model. Originally livestreamed at: https://twitch.tv/stephen_wolfram Stay up-to-date on this project by visiting our website: http://wolfr.am/physics Check out the announcement post: http://
From playlist Wolfram Physics Project Livestream Archive

Wolfram Physics Project: Working Session Thursday, June 4, 2020 [New Emerging Understandings]
This is a Wolfram Physics Project working session on new emerging understandings in the Wolfram Model with general Q&A. Originally livestreamed at: https://twitch.tv/stephen_wolfram Stay up-to-date on this project by visiting our website: http://wolfr.am/physics Check out the announcemen
From playlist Wolfram Physics Project Livestream Archive

What We've Learned from NKS Chapter 5: Two Dimensions and Beyond
In this episode of "What We've Learned from NKS", Stephen Wolfram is counting down to the 20th anniversary of A New Kind of Science with [another] chapter retrospective. If you'd like to contribute to the discussion in future episodes, you can participate through this YouTube channel or th
From playlist Science and Research Livestreams

Cryptography - Seminar 1 - Foundations
This seminar series is about the mathematical foundations of cryptography. In the first seminar Eleanor McMurtry introduces cryptography and explains some of the problems that need to be solved in order to develop proper foundations. The webpage for this seminar is https://lnor.net/uc-sem
From playlist Metauni

What We've Learned from NKS Chapter 3: The World of Simple Programs
In this episode of "What We've Learned from NKS", Stephen Wolfram is counting down to the 20th anniversary of A New Kind of Science with [another] chapter retrospective. If you'd like to contribute to the discussion in future episodes, you can participate through this YouTube channel or th
From playlist Science and Research Livestreams
