Automatic Pattern Matching for 3D Geometry in Blender
To help refining the alignment of multiple 3D scans with each other, I have written a new tool for Blender which automatically finds the best fit for mesh objects.
From playlist Random Blender Tests

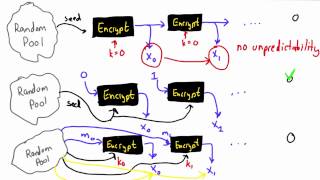
Randomness - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Random Oracle - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Blender test: Simple parallax mapping through composite and material nodes only
The original render output is flat. :) For similar technique see the node setups here: http://www.blendpolis.de/viewtopic.php?f=14&t=25226 http://www.kaikostack.com
From playlist Random Blender Tests

This lesson introduces the different sample methods when conducting a poll or survey. Site: http://mathispower4u.com
From playlist Introduction to Statistics
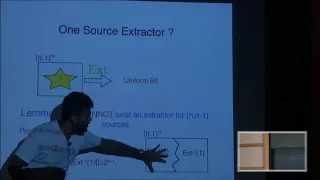
Towards optimal Ramsey graphs and randomness extractors - Eshan Chattopadhyay
Short talks by postdoctoral members Topic: Towards optimal Ramsey graphs and randomness extractors Speaker: Eshan Chattopadhyay Affiliation: Member, School of Mathematics Date: September 26, 2017 For more videos, please visit http://video.ias.edu
From playlist Mathematics
Pseudo Random Number Generator Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Recent Progress in Randomness Extraction - Eshan Chattopadhyay
Computer Science/Discrete Mathematics Seminar II Topic: Recent Progress in Randomness Extraction Speaker: Eshan Chattopadhyay Affiliation: Cornell University Date: March 07, 2023 Randomness is a vital resource in computation, with many applications in areas such as cryptography, data-str
From playlist Mathematics

PMSP - Computational pseudo-randomness and extractors I - Russell Impagliazzo
Russell Impagliazzo UC San Diego and Institute for Advanced Study June 14, 2010 For more videos, visit http://video.ias.edu
From playlist Mathematics

Nexus Trimester - Iftach Haitner (Tel Aviv University) - Leo Reyzin (Boston University) 2/3
Computational Analogues of Entropy 2/3 Iftach Haitner (Tel Aviv University) Leo Reyzin (Boston University) MArch 21, 2016 Abstract: If you see a cryptographic hash of my password, how can I quantify your uncertainty about the password? Entropy – a traditional measure of uncertainty – is
From playlist Nexus Trimester - 2016 - Secrecy and Privacy Theme

Near-Optimal Strong Dispersers - Dean Doron
Computer Science/Discrete Mathematics Seminar I Topic: Near-Optimal Strong Dispersers Speaker: Dean Doron Affiliation: The University of Texas at Austin Date: February 4, 2019 For more video please visit http://video.ias.edu
From playlist Mathematics

Live CEOing Ep 532: Design Review of MoleculeFingerprint and Other Functions
In this episode of Live CEOing, Stephen Wolfram discusses upcoming improvements and features to the Wolfram Language. If you'd like to contribute to the discussion in future episodes, you can participate through this YouTube channel or through the official Twitch channel of Stephen Wolfram
From playlist Behind the Scenes in Real-Life Software Design

Live CEOing Ep 438: Machine Learning Design Review for Wolfram Language 12.3
In this episode of Live CEOing, Stephen Wolfram reviews the design of improvements made to machine learning and neural network functions for the Wolfram Language. If you'd like to contribute to the discussion in future episodes, you can participate through this YouTube channel or through t
From playlist Behind the Scenes in Real-Life Software Design

PMSP - Computational pseudo-randomness and extractors II - Russell Impagliazzo
Russell Impagliazzo Institute for Advanced Study June 14, 2010 For more videos, visit http://video.ias.edu
From playlist Mathematics

Zero Knowledge Proofs - Seminar 1 - Introduction
This seminar series is about the mathematical foundations of cryptography. In this series Eleanor McMurtry is explaining Zero Knowledge Proofs (ZKPs), a fascinating set of techniques that allow one participant to prove they know something *without revealing the thing*. You can join this s
From playlist Metauni

True Randomness: Its Origin and Expansion - Yaoyun Shi
True Randomness: Its Origin and Expansion Yaoyun Shi University of Michigan April 21, 2014 How can we produce randomness of almost perfect quality, in large quantities, and under minimal assumptions? This question is fundamental not only to modern day information processing but also to phy
From playlist Mathematics

Randomness Quiz - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography