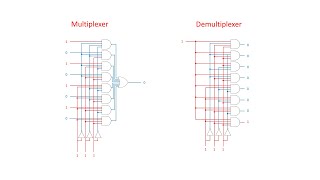
Dynamic Random Access Memory (DRAM). Part 4: Multiplexers and Demultiplexers
This is the fourth in a series of computer science videos is about the fundamental principles of Dynamic Random Access Memory, DRAM, and the essential concepts of DRAM operation. This video covers multiplexers and demultiplexers. It describes what these electronic circuits do and some of
From playlist Random Access Memory

Random Oracle - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Randomness Extraction: A Survey - David Zuckerman
David Zuckerman University of Texas at Austin; Institute for Advanced Study February 7, 2012 A randomness extractor is an efficient algorithm which extracts high-quality randomness from a low-quality random source. Randomness extractors have important applications in a wide variety of area
From playlist Mathematics
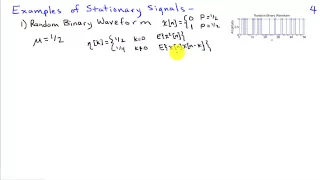
Random Processes and Stationarity
http://AllSignalProcessing.com for more great signal-processing content: ad-free videos, concept/screenshot files, quizzes, MATLAB and data files. Introduction to describing random processes using first and second moments (mean and autocorrelation/autocovariance). Definition of a stationa
From playlist Random Signal Characterization

Randomness - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Dynamic Random Access Memory (DRAM). Part 3: Binary Decoders
This is the third in a series of computer science videos is about the fundamental principles of Dynamic Random Access Memory, DRAM, and the essential concepts of DRAM operation. This video covers the role of the row address decoder and the workings of generic binary decoders. It also expl
From playlist Random Access Memory

Randomness Quiz - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography
If you are interested in learning more about this topic, please visit http://www.gcflearnfree.org/ to view the entire tutorial on our website. It includes instructional text, informational graphics, examples, and even interactives for you to practice and apply what you've learned.
From playlist Machine Learning

Questions And Answers - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography
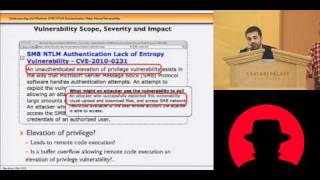
Black Hat USA 2010: Understanding the Windows SMB NTLM Weak Nonce Vulnerability 5/5
Speakers: Hernan Ochoa, Agustin Azubel In February 2010, we found a vulnerability in the SMB NTLM Windows Authentication mechanism that have been present in Windows systems for at least 14 years (from Windows NT 4 to Windows Server 2008). You probably haven't heard about this vulnerabilit
From playlist BH USA 2010 - OS WARS

DEFCON 16: Anti-RE Techniques in DRM Code
Speaker: Jan Newger, Security Researcher In order to prevent music from being copied among consumers, content providers often use DRM systems to protect their music files. This talk describes the approach taken while analysing a DRM system (whose identity needs to be kept secret due to le
From playlist DEFCON 16

Computer Security | What Is Computer Security | Cyber Security Tutorial | Simplilearn
🔥Advanced Executive Program In Cybersecurity: https://www.simplilearn.com/pgp-advanced-executive-program-in-cyber-security?utm_campaign=ComputerSecurity-cs3B0zcRJco&utm_medium=Descriptionff&utm_source=youtube 🔥Caltech Cybersecurity Bootcamp(US Only): https://www.simplilearn.com/cybersecuri
From playlist Cyber Security Playlist [2023 Updated]🔥

Live Coding Project: Create a Random Quote Machine using Vue.js - with Gwen Faraday
Watch live as Gwen Faraday uses Vue.js to create a Random Quote Machine. Git Repo for the project: https://github.com/gwenf/freecodecamp-projects-vue Check out Gwen's channel here: https://www.youtube.com/channel/UCxA99Yr6P_tZF9_BgtMGAWA -- Learn to code for free and get a developer jo
From playlist Vue.js Live Coding with Gwen

EEVBlog #1075 - Digital BitBox Hardware Wallet Review
Review of the Digital BitBox crypto bitcoin hardware wallet, made in Switzerland. Bitcoin donations appreciated: 12gVrtZg75SWQFKhQ512DjPKpSFt3sK218 http://www.MyWallet.ch https://kit.com/EEVblog/crypto-hardware https://shiftcrypto.ch/ Forum: http://www.eevblog.com/forum/blog/eevblog-107
From playlist Product Reviews & Teardowns

Non-Black-Box Derandomization - Roei Tell
Computer Science/Discrete Mathematics Seminar II Topic: Non-Black-Box Derandomization Speaker: Roei Tell Affiliation: Member, School of Mathematics Date: March 01, 2022 This is the third and final talk in the joint series with Lijie Chen. The talk will NOT rely on the technical contents
From playlist Mathematics

Computer History IBM 305 RAMAC and 650 RAMAC, 1956 (350 Disk Storage)
Two vintage 1956 IBM films: (1) the IBM 305 RAMAC, the first commercial computer using moving-head hard disk drive for secondary storage via the IBM 350 disk unit; and (2) the IBM 650 RAMAC, which used the IBM 650 computer with an upgraded RAMAC disk drive system. The IBM 350 Disk Unit was
From playlist Computer History: Early IBM computers 1944 to 1970's
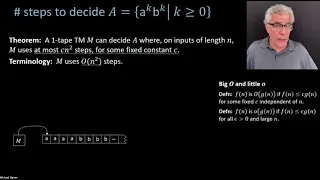
MIT 18.404J Theory of Computation, Fall 2020 Instructor: Michael Sipser View the complete course: https://ocw.mit.edu/18-404JF20 YouTube Playlist: https://www.youtube.com/playlist?list=PLUl4u3cNGP60_JNv2MmK3wkOt9syvfQWY Quickly reviewed last lecture. Gave an introduction to complexity the
From playlist MIT 18.404J Theory of Computation, Fall 2020

Lecture 2: Models of Computation, Document Distance
MIT 6.006 Introduction to Algorithms, Fall 2011 View the complete course: http://ocw.mit.edu/6-006F11 Instructor: Erik Demaine License: Creative Commons BY-NC-SA More information at http://ocw.mit.edu/terms More courses at http://ocw.mit.edu
From playlist MIT 6.006 Introduction to Algorithms, Fall 2011

22C3: Covert channels in TCP/IP: attack and defense
Speaker: Steven J. Murdoch Creation and detection of IP steganography for covert channels and device fingerprinting This talk will show how idiosyncrasies in TCP/IP implementations can be used to reveal the use of several steganography schemes, and how they can be fixed. The analysis can
From playlist 22C3: Private Investigations
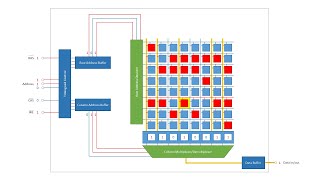
Dynamic Random Access Memory (DRAM). Part 2: Read and Write Cycles
This is the second in a series of computer science videos is about the fundamental principles of Dynamic Random Access Memory, DRAM, and the essential concepts of DRAM operation. This video covers stages of the read cycle and the write cycle including memory address multiplexing as a means
From playlist Random Access Memory