
C49 Example problem solving a system of linear DEs Part 1
Solving an example problem of a system of linear differential equations, where one of the equations is not homogeneous. It's a long problem, so this is only part 1.
From playlist Differential Equations

Solve a system with three variables
👉Learn how to solve a system of three linear systems. A system of equations is a set of equations which are to be solved simultaneously. A linear equation is an equation whose graph is a straight line. The solution to a system of equations is a set of unique values of the variables for wh
From playlist Solve a System of Equations With Three Variables

How to use a system of equations to solve a word problem
👉Learn how to solve a system of linear equations from a word problem. A system of equations is a set of more than one equations which are to be solved simultaneously. A word problem is a real world simulation of a mathematical concept. The solution to a system of equation is the set of val
From playlist Solve a System Algebraically | Algebra 2

Learn how to graph a word problem system of inequalities
👉Learn how to solve a system of linear equations from a word problem. A system of equations is a set of more than one equations which are to be solved simultaneously. A word problem is a real world simulation of a mathematical concept. The solution to a system of equation is the set of val
From playlist Solve a System Algebraically | Algebra 2

Solve Linear Systems of Equations
How to solve linear systems via matrices. We discuss consistent and inconsistent forms and show how to solve.
From playlist Intro to Linear Systems

What are the three types of solutions to a system of equations
👉Learn about solving a system of equations by graphing. A system of equations is a set of more than one equations which are to be solved simultaneously. To solve a system of equations graphically, we graph the individual equations making up the system. The point of intersection of the gr
From playlist Solve a System of Equations by Graphing | Learn About

When do linear systems have solutions?
How to determine the solution structure to a linear system of simultaneous equations. Several examples are discussed.
From playlist Intro to Linear Systems

Speakers: djb | Nadia Heninger | Tanja Lange RSA factorization in the real world RSA is the dominant public-key cryptosystem on the Internet. This talk will explain the state of the art in techniques for the attacker to figure out your secret RSA keys. A typical 1024-bit RSA public key
From playlist 29C3: Not my department

From playlist Week 2 2015 Shorts

The large number "RSA-129" posed a challenge experts said would take 40 quadrillion years to solve - but took 17. Featuring Ron Rivest, co-inventor of RSA... More links below... Our original RSA video (how it all works): https://youtu.be/M7kEpw1tn50 More from Ron from this interview (qua
From playlist Cryptography on Numberphile and Computerphile
#MegaFavNumbers : RSA's Unsolvable Modulus
RSA was the first Public Key Cryptosystem available to the public. Despite massive improvements, both to the security of RSA and the Public key crypto itself, RSA is still -the- benchmark people tend to learn about first. Now find out why RSA-2048 is one of my #MegaFavNumbers. #MegaFavNum
From playlist MegaFavNumbers
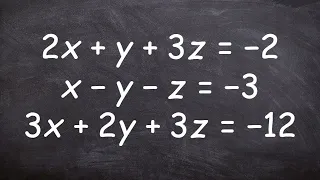
Solve a system of three variables
👉Learn how to solve a system of three linear systems. A system of equations is a set of equations which are to be solved simultaneously. A linear equation is an equation whose graph is a straight line. The solution to a system of equations is a set of unique values of the variables for wh
From playlist Solve a System of Equations With Three Variables

Discrete Structures: Digital certificates and implementing RSA
Our last session on RSA and public key cryptography. We'll learn about digital certificates and see how to implement the core RSA algorithms in Python.
From playlist Discrete Structures, Spring 2022

Lecture - 33 Basic Cryptographic Concepts Part : II
Lecture Series on Internet Technologies by Prof.I.Sengupta, Department of Computer Science & Engineering ,IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Cryptography, Security

Key Exchange Problems - Computerphile
Diffie Hellman has a flaw. Dr Mike Pound explains how a man in the middle could be a big problem, unless we factor it in... Public Key Cryptography: https://youtu.be/GSIDS_lvRv4 Elliptic Curve Cryptography: Coming Soon! https://www.facebook.com/computerphile https://twitter.com/compute
From playlist Cryptography on Numberphile and Computerphile

Kernel Recipes 2018 - TPM enabling the Crypto Ecosystem for enhanced Security - James Bottomley
For decades, all laptops have come with a TPM. Now with Microsoft forcing the transition to the next generation, Linux faces a challenge in that all the previous TPM 1.2 tools don’t work with 2.0. Having to create new tools for TPM 2.0 also provides the opportunity to integrate the TPM
From playlist Kernel Recipes 2018

Neural RSA | Stanford CS224U Natural Language Understanding | Spring 2021
For more information about Stanford’s Artificial Intelligence professional and graduate programs, visit: https://stanford.io/ai To learn more about this course visit: https://online.stanford.edu/courses/cs224u-natural-language-understanding To follow along with the course schedule and s
From playlist Stanford CS224U: Natural Language Understanding | Spring 2021

Solve a system of three equations with no solutions
👉Learn how to solve a system of three linear systems. A system of equations is a set of equations which are to be solved simultaneously. A linear equation is an equation whose graph is a straight line. The solution to a system of equations is a set of unique values of the variables for wh
From playlist Solve a System of Equations With Three Variables

🔥Digital Marketing Masterclass: How to Test and Control Responsive Search Ads | 2023 | Simplilearn
🔥Enroll on Free Digital Marketing Course & Get Your Completion Certificate: https://www.simplilearn.com/learn-digital-marketing-fundamentals-basics-skillup?utm_campaign=DigitalMarketingWebinar11Oct22&utm_medium=ShortsDescription&utm_source=youtube About the Webinar: Keep your digi
From playlist Simplilearn Live

C50 Example problem solving a system of linear DEs Part 2
Part 2 of the prvious example problem, solving a system of linear differential equations, where one of the equations is non-homogeneous.
From playlist Differential Equations