
Excellent Proof Writing Book For Beginners
This is a newer book that is absolutely amazing for anyone who wants to learn to write proofs. If you are learning on your own then this book is definitely worth picking up. If you are taking a class on proof writing then it's also extremely helpful. Learning to write proofs takes a lot of
From playlist Book Reviews
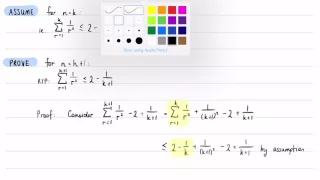
Inequality Proof: Summing Reciprocals of Squares (Experimental Silent Screencast)
via YouTube Capture
From playlist The Nature of Proof

Mathematical Notations -- How to do mathematical proofs (PART 2)
This video contains the preliminary mathematical notation that will be used in the course. This is preliminary video (part 0) on a series of videos: How to do mathematical proofs. The course is structured in such a way to make the transition from applied-style problems in mathematics (som
From playlist How to do Mathematical Proofs

Geometry - Ch. 3: Proofs (2 of 17) What is the KEY to Performing Proofs in Geometry? 2
Visit http://ilectureonline.com for more math and science lectures! In this video I will explain what is the key to performing proofs in geometry. The key is learning the language of proofs in geometry. I will also explain the 3-column method (statement, what we are doing?, and why we do
From playlist GEOMETRY CH 3 PROOFS

Proof: What is it, and how does it work?
From playlist The Nature of Proof

Introduction to Proof Methods!
The first video I've made on proof methods! I discuss what a proof is, give some general tips, show how to prove a conditional statement using the direct proof method, and use the direct proof method to do some very beginner friendly proofs! The goals of this video: 1. Help people underst
From playlist Proofs

Examples of Proof by Contradiction -- How to do Mathematical Proofs (PART 7)
This is the fifth video on a series of videos on: How to do mathematical proofs. The course is structured in such a way to make the transition from applied-style problems in mathematics (sometimes referred to as engineering mathematics) to pure mathematics much smoother. The course will
From playlist How to do Mathematical Proofs
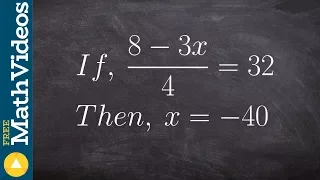
Learning to write an algebraic proof
👉 Learn how to write an algebraic proof. Algebraic proofs are used to help students understand how to write formal proofs where we have a statement and a reason. In the case of an algebraic proof the statement will be the operations used to solve an algebraic equation and the reason will
From playlist Parallel Lines and a Transversal

Geometry - Ch. 3: Proofs (1 of 17) What is the KEY to Performing Proofs in Geometry? 1
Visit http://ilectureonline.com for more math and science lectures! In this video I will explain what is the key to performing proofs in geometry. The key is learning the language of proofs in geometry. 1 To donate: http://www.ilectureonline.com/donate https://www.patreon.com/user?u=3236
From playlist GEOMETRY CH 3 PROOFS

RustConf 2017 - Fast, Safe, Pure-Rust Elliptic Curve Cryptography
Fast, Safe, Pure-Rust Elliptic Curve Cryptography by Isis Lovecruft & Henry De Valence This talk discusses the design and implementation of curve25519-dalek, a pure-Rust implementation of operations on the elliptic curve known as Curve25519. We will discuss the goals of the library and g
From playlist RustConf 2017

RustConf 2017 - Fast, Safe, Pure-Rust Elliptic Curve Cryptography
Fast, Safe, Pure-Rust Elliptic Curve Cryptography by Isis Lovecruft & Henry De Valence This talk discusses the design and implementation of curve25519-dalek, a pure-Rust implementation of operations on the elliptic curve known as Curve25519. We will discuss the goals of the library and gi
From playlist RustConf 2017

Séminaire Bourbaki - 21/06/2014 - 3/4 - Thomas C. HALES
Developments in formal proofs A for mal proof is a proof that can be read and verified by computer, directly from the fundamental rules of logic and the foundational axioms of mathematics. The technology behind for mal proofs has been under development for decades and grew out of efforts i
From playlist Bourbaki - 21 juin 2014
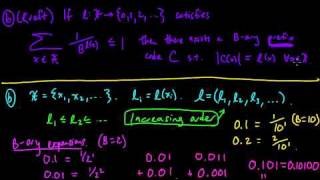
(IC 2.10) Kraft-McMillan - examples for (b)
For a given set of lengths, the Kraft-McMillan inequality is a necessary condition for the existence of a uniquely decodable code, and a sufficient condition for the existence of a prefix code. A playlist of these videos is available at: http://www.youtube.com/playlist?list=PLE125425EC83
From playlist Information theory and Coding
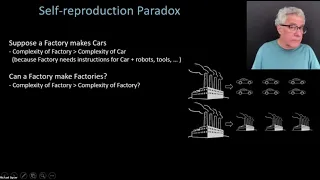
11. Recursion Theorem and Logic
MIT 18.404J Theory of Computation, Fall 2020 Instructor: Michael Sipser View the complete course: https://ocw.mit.edu/18-404JF20 YouTube Playlist: https://www.youtube.com/playlist?list=PLUl4u3cNGP60_JNv2MmK3wkOt9syvfQWY Quickly reviewed last lecture. Discussed self-reference and the recur
From playlist MIT 18.404J Theory of Computation, Fall 2020
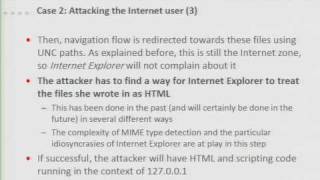
Black Hat DC 2010: Internet Explorer turns your personal computer into a public file server 4/7
Clip 4/7 Speakers: Jorge Luis, Alvarez Medina In this presentation we will show how an attacker can read every file of your file system if you are using Internet Explorer. This attack leverages different design features of Internet Explorer entailing security risks that, while low if c
From playlist Black Hat DC 2010
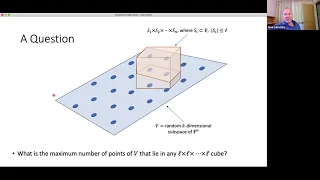
Thresholds for Random Subspaces, aka, LDPC Codes Achieve List-Decoding Capacity - Mary Wootters
Computer Science/Discrete Mathematics Seminar I Topic: Thresholds for Random Subspaces, aka, LDPC Codes Achieve List-Decoding Capacity Speaker: Mary Wootters Affiliation: Stanford University Date: November 30, 2020 For more video please visit http://video.ias.edu
From playlist Mathematics

27c3: Defense is not dead (en)
Speaker: Andreas Bogk Why we will have more secure computers - tomorrow The security model of our current computer architectures - kernel in ring 0, processes in ring 3 - goes back to the early 70s. However, science hasn't stopped. This talk is going to look into the state of the art in
From playlist 27C3: We come in peace

Fabian Immler, Carnegie Mellon University Formal mathematics and a proof of chaos Formal proof has been successfully applied to the verification of hardware and software systems. But formal proof is also applicable to mathematics: proofs can be checked with ultimate rigor and one can bui
From playlist Fall 2019 Kolchin Seminar in Differential Algebra
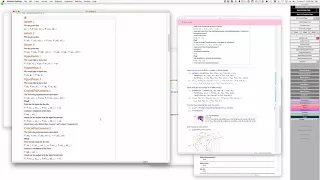
Live CEOing Ep 09: Representing Proofs in the Wolfram Language
Watch Stephen Wolfram and teams of developers in a live, working, language design meeting. This episode is about Representing Proofs in the Wolfram Language.
From playlist Behind the Scenes in Real-Life Software Design
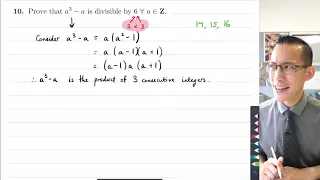
Proof: a³ - a is always divisible by 6 (2 of 2: Proof by exhaustion)
More resources available at www.misterwootube.com
From playlist The Nature of Proof