
23 Algebraic system isomorphism
Isomorphic algebraic systems are systems in which there is a mapping from one to the other that is a one-to-one correspondence, with all relations and operations preserved in the correspondence.
From playlist Abstract algebra

Equivalence Relations Definition and Examples
Please Subscribe here, thank you!!! https://goo.gl/JQ8Nys Equivalence Relations Definition and Examples. This video starts by defining a relation, reflexive relation, symmetric relation, transitive relation, and then an equivalence relation. Several examples are given.
From playlist Abstract Algebra

In this video we finish with three more example of calculating the null space of a matrix. These three example help us gain an even deeper insight into the null space by consider how many special cases we will get. Remember that the linear combinations of the special cases give us the nu
From playlist Introducing linear algebra

This shows an interactive illustration that explains that parallel vectors can have either the same or opposite directions. The clip is from the book "Immersive Linear Algebra" at http://www.immersivemath.com
From playlist Chapter 2 - Vectors
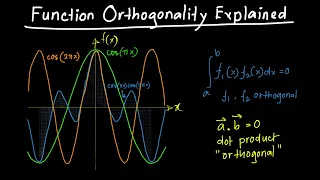
Function Orthogonality Explained
https://www.patreon.com/edmundsj If you want to see more of these videos, or would like to say thanks for this one, the best way you can do that is by becoming a patron - see the link above :). And a huge thank you to all my existing patrons - you make these videos possible. In this video
From playlist Optoelectronic and Photonic Devices
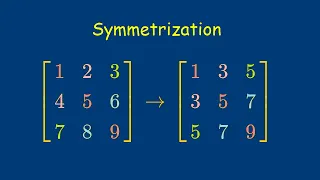
In this video, I define a cool operation called the symmetrization, which turns any matrix into a symmetric matrix. Along the way, I also explain how to show that an (abstract) linear transformation is one-to-one and onto. Finally, I show how to decompose and matrix in a nice way, sort of
From playlist Linear Transformations

Algebraic inverse proportion 1
Powered by https://www.numerise.com/ Algebraic inverse proportion 1
From playlist Proportion

Nexus Trimester - Manoj Prabhakaran (University of Illinois) - 1/2
Some Capacity Question in MPC - 1/2 Manoj Prabhakaran (University of Illinois) March 28, 2016 Abstract: Secure multiparty computation allows two or more parties to perform a distributed computation on their local inputs while hiding the inputs from each other. This part of the minicourse
From playlist Nexus Trimester - 2016 - Secrecy and Privacy Theme

Lec 24 | MIT 6.046J / 18.410J Introduction to Algorithms (SMA 5503), Fall 2005
Lecture 24: Advanced Topics (cont.) View the complete course at: http://ocw.mit.edu/6-046JF05 License: Creative Commons BY-NC-SA More information at http://ocw.mit.edu/terms More courses at http://ocw.mit.edu
From playlist MIT 6.046J / 18.410J Introduction to Algorithms (SMA 5503),

Lec 25 | MIT 6.046J / 18.410J Introduction to Algorithms (SMA 5503), Fall 2005
Lecture 25: Advanced Topics (cont.) | Discussion of Follow-on Classes View the complete course at: http://ocw.mit.edu/6-046JF05 License: Creative Commons BY-NC-SA More information at http://ocw.mit.edu/terms More courses at http://ocw.mit.edu
From playlist MIT 6.046J / 18.410J Introduction to Algorithms (SMA 5503),

Dakshita Khurana - Weakening Assumptions in Quantum Cryptography IV.b Part 2 of 2 - IPAM at UCLA
Recorded 29 July 2022. Dakshita Khurana of the University of Illinois at Urbana-Champaign presents "Weakening Assumptions in Quantum Cryptography IV.b" at IPAM's Graduate Summer School Post-quantum and Quantum Cryptography. Abstract: We will discuss how quantum information can be used to r
From playlist 2022 Graduate Summer School on Post-quantum and Quantum Cryptography
This shows an small game that illustrates the concept of a vector. The clip is from the book "Immersive Linear Algebra" at http://www.immersivemath.com
From playlist Chapter 2 - Vectors

Dakshita Khurana - Weakening Assumptions in Quantum Cryptography IV.a Part 1 of 2 - IPAM at UCLA
Recorded 29 July 2022. Dakshita Khurana of the University of Illinois at Urbana-Champaign presents "Weakening Assumptions in Quantum Cryptography IV. a" at IPAM's Graduate Summer School Post-quantum and Quantum Cryptography. Abstract: We will discuss how quantum information can be used to
From playlist 2022 Graduate Summer School on Post-quantum and Quantum Cryptography

Oblivious Transfer - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Solving Private Set Intersection via Cuckoo Hashing: Benny Pinkas, Bar-Ilan University, Israel
Private set intersection (PSI) allows two parties to compute the intersection of their sets without revealing any information about items that are not in the intersection. There has been considerable research on designing custom secure protocols for computing PSI, due to the fact that PSI
From playlist Turing Seminars

Stanford Seminar - Protecting Patient Privacy in Genomic Analysis
One of the challenges for patients with rare diseases is the lack of local data to use for analysis. As a result, patients are having to rely on 3rd party facilities to carry out the computations based on data collected around the globe. But due to patient privacy concerns, as well as heav
From playlist Stanford Seminars
The inverse of a matrix is a similarly sized matrix such that the multiplication of the two matrices results in the identity matrix. In this video we look at an example of this. You can learn more about Mathematica on my Udemy course at https://www.udemy.com/mathematica/ PS! Wait until
From playlist Introducing linear algebra

Online Learning in Reactive Environments - Raman Arora
Seminar on Theoretical Machine Learning Topic: Online Learning in Reactive Environments Speaker: Raman Arora Affiliation: Johns Hopkins University; Member, School of Mathematics Date: December 18, 2019 For more video please visit http://video.ias.edu
From playlist Mathematics

Systems of linear equations seek a common solution for the unknowns across more than one equation. It can be very simple to calculate a solution using simple algebra. Alternatively you can use elementary row operations or even lines and planes in two- and three-dimensional space. At th
From playlist Introducing linear algebra

15. Cache-Oblivious Algorithms
MIT 6.172 Performance Engineering of Software Systems, Fall 2018 Instructor: Julian Shun View the complete course: https://ocw.mit.edu/6-172F18 YouTube Playlist: https://www.youtube.com/playlist?list=PLUl4u3cNGP63VIBQVWguXxZZi0566y7Wf Prof. Shun discusses cache-oblivious algorithms throug
From playlist MIT 6.172 Performance Engineering of Software Systems, Fall 2018