
Other Public Key Cryptosystems: Part 1
Fundamental concepts of Diffie-Hellman Key exchange are discussed. ElGamal Cryptosystem is presented. Elliptic curves are Analyzed.
From playlist Network Security

Other Public Key Cryptosystems: Part 2
Fundamental concepts of Diffie-Hellman Key exchange are discussed. ElGamal Cryptosystem is presented. Elliptic curves are Analyzed.
From playlist Network Security

Cryptography is a complex and confusing subject. In this talk you will learn about the core components of cryptography used in software development: securing data with encryption, ensuring data integrity with hashes and digital signatures, and protecting passwords with key derivation funct
From playlist Blockchain

R11. Cryptography: More Primitives
MIT 6.046J Design and Analysis of Algorithms, Spring 2015 View the complete course: http://ocw.mit.edu/6-046JS15 Instructor: Ling Ren In this recitation, problems related to cryptography are discussed. License: Creative Commons BY-NC-SA More information at http://ocw.mit.edu/terms More c
From playlist MIT 6.046J Design and Analysis of Algorithms, Spring 2015

Cryptanalysis of Classical Ciphers
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security
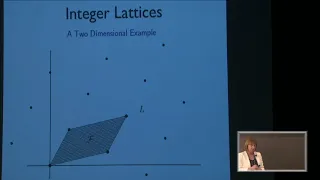
Mathematical Ideas in Lattice Based Cryptography - Jill Pipher
2018 Program for Women and Mathematics Topic: Mathematical Ideas in Lattice Based Cryptography Speaker: Jill Pipher Affiliation: Brown University Date: May 21, 2018 For more videos, please visit http://video.ias.edu
From playlist Mathematics

Few other Cryptanalytic Techniques
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Overview on S-Box Design Principles
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security
Math for Liberal Studies - Lecture 1.9 The Knapsack Problem
This video covers material from Math for Liberal Studies Section 1.9: The Knapsack Problem. In this video, I explain what the knapsack problem is, and we work through an example using a recursive algorithm to solve the problem.
From playlist Math for Liberal Studies Lectures

Knapsack Problem Using Dynamic Programming | 0/1 Knapsack Problem | Data Structures | Simplilearn
This video on knapsack Problem Using Dynamic Programming will acquaint you with a clear understanding of the fractional or 0-1 knapsack problem statement and solution implementation. In this Data Structure Tutorial, you will understand why the difference between 0-1 knapsack and fractional
From playlist Data Structures & Algorithms

0/1 Knapsack problem | Dynamic Programming
Overview of the 0/1 Knapsack problem using dynamic programming Algorithms repository: https://github.com/williamfiset/algorithms My website: http://www.williamfiset.com
From playlist Dynamic Programming

Knapsack, Bandwidth Min. Intro: Greedy Algorithms - Lecture 14
All rights reserved for http://www.aduni.org/ Published under the Creative Commons Attribution-ShareAlike license http://creativecommons.org/licenses/by-sa/2.0/ Tutorials by Instructor: Shai Simonson. http://www.stonehill.edu/compsci/shai.htm Visit the forum at: http://www.coderisland.c
From playlist ArsDigita Algorithms by Shai Simonson

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Steganography Tutorial - Hide Messages In Images
Steganography is the hiding of a secret message within an ordinary message and the extraction of it at its destination. Steganography takes cryptography a step further by hiding an encrypted message so that no one suspects it exists. Ideally, anyone scanning your data will fail to know it
From playlist Ethical Hacking & Penetration Testing - Complete Course

0-1 Knapsack Problem (Dynamic Programming)
Dynamic Programming Tutorial with 0-1 Knapsack Problem
From playlist Dynamic Programming Tutorial Series

1. Introduction, Optimization Problems (MIT 6.0002 Intro to Computational Thinking and Data Science)
MIT 6.0002 Introduction to Computational Thinking and Data Science, Fall 2016 View the complete course: http://ocw.mit.edu/6-0002F16 Instructor: John Guttag Prof. Guttag provides an overview of the course and discusses how we use computational models to understand the world in which we li
From playlist MIT 6.0002 Introduction to Computational Thinking and Data Science, Fall 2016

Heiko Röglin: Smoothed Analysis of Algorithms (Part 2)
The lecture was held within the framework of the Hausdorff Trimester Program: Combinatorial Optimization
From playlist HIM Lectures 2015

Adam Polak: Knapsack and Subset Sum with Small Items
Knapsack and Subset Sum are fundamental NP-hard problems in combinatorial optimization. Recently there has been a growing interest in understanding the best possible pseudopolynomial running times for these problems with respect to various parameters. In this paper we focus on the maximum
From playlist Workshop: Parametrized complexity and discrete optimization

An informal introduction to cryptography. Part of a larger series teaching programming at http://codeschool.org
From playlist Cryptography