
Definition of an Injective Function and Sample Proof
We define what it means for a function to be injective and do a simple proof where we show a specific function is injective. Injective functions are also called one-to-one functions. Useful Math Supplies https://amzn.to/3Y5TGcv My Recording Gear https://amzn.to/3BFvcxp (these are my affil
From playlist Injective, Surjective, and Bijective Functions
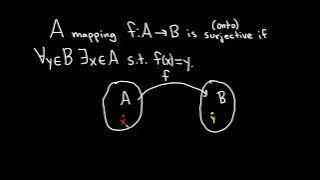
Definition of a Surjective Function and a Function that is NOT Surjective
We define what it means for a function to be surjective and explain the intuition behind the definition. We then do an example where we show a function is not surjective. Surjective functions are also called onto functions. Useful Math Supplies https://amzn.to/3Y5TGcv My Recording Gear ht
From playlist Injective, Surjective, and Bijective Functions
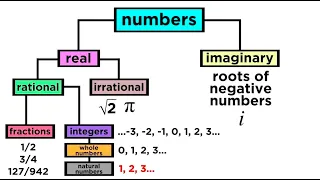
What are the Types of Numbers? Real vs. Imaginary, Rational vs. Irrational
We've mentioned in passing some different ways to classify numbers, like rational, irrational, real, imaginary, integers, fractions, and more. If this is confusing, then take a look at this handy-dandy guide to the taxonomy of numbers! It turns out we can use a hierarchical scheme just lik
From playlist Algebra 1 & 2

Injective, Surjective and Bijective Functions (continued)
This video is the second part of an introduction to the basic concepts of functions. It looks at the different ways of representing injective, surjective and bijective functions. Along the way I describe a neat way to arrive at the graphical representation of a function.
From playlist Foundational Math

What is an Injective Function? Definition and Explanation
An explanation to help understand what it means for a function to be injective, also known as one-to-one. The definition of an injection leads us to some important properties of injective functions! Subscribe to see more new math videos! Music: OcularNebula - The Lopez
From playlist Functions

This tutorial explains the different types of numbers commonly used in algebra. The number types discussed are counting, whole, integer, rational, irrational, and imaginary. Join this channel to get access to perks: https://www.youtube.com/channel/UCn2SbZWi4yTkmPUj5wnbfoA/join :)
From playlist Basic Math

In this tutorial I cross the bridge between a standard algebraic function and products sets, as well as mappings. I show the three types of mappings, namely injective (one-to-one), surjective (onto), and their combination, a bijection.
From playlist Abstract algebra

Lesson 02_03 Abstract and concrete types
Download the notebook files as they are added at: http://www.juanklopper.com/computer-programming/ All types are either concrete (that is a type right at the bottom of the tree of types) or abstract (basically everything higher up the tree). Concrete types are what we work with. We can c
From playlist The Julia Computer Language

Easy Rust 080: Enumerate and how iterators are made
The enumerate method and how Rust puts iterators together. From this chapter: https://dhghomon.github.io/easy_rust/Chapter_37.html #rustlang Want to buy me a coffee? Do it here: https://www.buymeacoffee.com/mithridates
From playlist Easy Rust / Rust in a Month of Lunches: bite-sized Rust tutorials

Enumeration in C Programming | enum In C Language | C Programming For Beginners | Simplilearn
This video by Simplilearn will explain to you Enumeration in C Programming. enum In C Language Programming tutorial will help you learn enumeration definition in c, how to use enum. This C programming tutorial will cover both theoretical and practical demonstrations for a better learning e
From playlist C++ Tutorial Videos

Linux Essentials For Hackers - #8 - Enumerating Distribution & Kernel Information
Welcome to the Linux Essentials For Hackers series, where we will be covering the 20% you need to know to be efficient with Linux. In this video, we will be covering how to enumerate distribution & kernel information in Linux. This series is sponsored by Linode, use the link below to get
From playlist Linux Essentials For Hackers

DNS Enumeration Tutorial - Dig, Nslookup & Host
Hey guys! HackerSploit here back again with another video, in this video, I will be showing you how to use Dig, Nslookup & host to perform DNS enumeration/reconnaissance. Our Platforms: Hsploit: https://hsploit.com/ HackerSploit Forum: https://hackersploit.org/ HackerSploit Academy: https
From playlist Ethical Hacking & Penetration Testing - Complete Course

Unity - lesson 15 - coroutines
From playlist Unity game engine

(UPDATED) LaTeX Tutorial 4 - Creating Lists
In this updated tutorial, I show you how to use LaTeX to create numbered and bulleted lists. To follow along with this tutorial I recommend using one of the following: (1) Overleaf: https://www.overleaf.com/?r=b4398ca7&rm=d&rs=b (2) TexMaker: https://www.xm1math.net/texmaker/ Warning! If
From playlist LaTeX Tutorials (featuring Texmaker)

Swift 2 Tutorial | Swift 2 Optionals | Swift 2 Binding | Swift 2 Code Safety | Swift 2 Enumerations
This video explains the basic of Swift 2.0 programming. It talks about the concepts like Swift 2.0 Optionals, Swift 2.0 Binding, Swift 2.0 Enumerations and Swift 2.0 Code Safety Objectives and Outcomes of the video " - Create app - Understand the app creation process - Create a new class
From playlist iOS App Development Tutorial Videos

Introduction To Pentesting - Enumeration
In this video, I demonstrate how to perform service enumeration with Nmap scripts. The target box that is used in this video is Metasploitable2. Metasploitable is an intentionally vulnerable Linux virtual machine. This VM can be used to conduct security training, test security tools, and p
From playlist Ethical Hacking & Penetration Testing - Complete Course

Ethical Hacking Tutorial | Comprehensive Subdomain Enumeration | Session 03 | #cybersecurity
Don’t forget to subscribe! This ethical hacking tutorial series is about comprehensive subdomain enumeration. Through this tutorial series, I will be demonstrating how to install, configure and use different tools for subdomain enumeration. We will try to go through the following subdom
From playlist Comprehensive Subdomain Enumeration
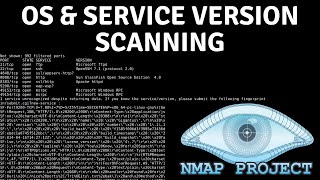
Nmap - OS And Service Version Scanning
In this video, I demonstrate how to perform OS and service version scanning and detection with Nmap. Nmap is a free and open-source network scanner created by Gordon Lyon. Nmap is used to discover hosts and services on a computer network by sending packets and analyzing the responses. Nmap
From playlist Ethical Hacking & Penetration Testing - Complete Course

Isomorphisms in abstract algebra
In this video I take a look at an example of a homomorphism that is both onto and one-to-one, i.e both surjective and injection, which makes it a bijection. Such a homomorphism is termed an isomorphism. Through the example, I review the construction of Cayley's tables for integers mod 4
From playlist Abstract algebra
